Our post, “Three Strategic Steps to a Threat Informed Defense,” highlights the reasons for and merits of moving to a threat-informed defense (TiD) approach. A TiD centers on the use of MITRE ATT&CK®, a globally accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base forms a foundation for developing specific threat models and methodologies in the private sector, government, and cybersecurity product and service community.1
In this post, we're leveraging MITRE ATT&CK to illustrate how to apply the tenets of a TiD to track adversary tactics, techniques, and procedures (TTPs) against something near and dear to us all, the supply chain. After all, your organization should have a priority intelligence requirement (PIR) to understand the threats to your supply chain, the vulnerabilities in your supply chain, and the impact and likelihood of an attack against your supply chain.
A supply chain of attack?
The supply chain is rapidly becoming the Achilles heel of every organization, particularly as a target by sophisticated threat actors such as APT29 (COZY BEAR or The Dukes). Significant vulnerabilities such as SolarWinds (2020) and Log4J (2021) call attention to the brittle nature of today's supply chains. As Crowdstrike recently stated, "Supply chain compromises are an increasing threat that impacts a range of sectors, with threat actors leveraging access to support several motivations including financial gain (such as with the Kaseya ransomware attack) and espionage."2
To illustrate the power of MITRE ATT&CK to defend your supply chain, we're using a hypothetical attack carried out by APT29, using the Cobalt Strike (CS) malware family.
Who's calling home?
Red alert! Red alert! All hands on deck.
Our scenario starts with suspicious traffic uncovered by your security operations center (SOC). Specifically, your sensors detect outbound encrypted traffic going to a suspicious location.
Based on this alert, your network defenders need to quickly understand if this is an isolated event or part of a more complex attack by one or more threat actors.
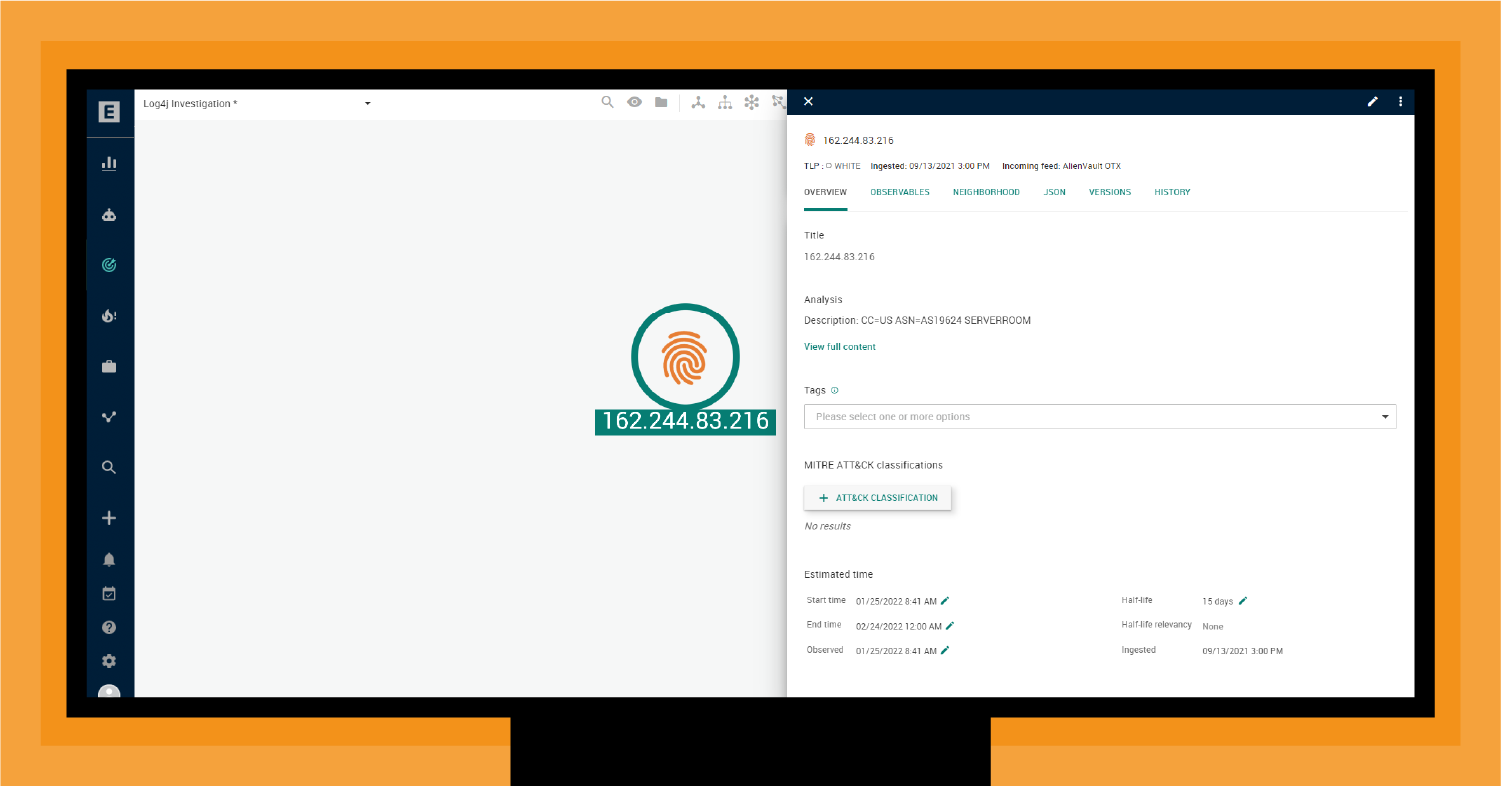
Your SOC ships this information over to your CTI analysts, who leverage EclecticIQ Intelligence Center to determine how this indicator aligns with known threats. This allows them to better assess what already happened, what else might be happening, and what might happen next.
EclecticIQ Intelligence Center is a CTI solution encompassing an advanced threat intelligence manager, add-on curated intelligence feeds, and a collaborative analyst workbench. EclecticIQ Intelligence Center unites machine-powered threat data processing and dissemination with human-led data analysis to prioritize and manage intelligence.
EclecticIQ Intelligence immediately aligns this indicator with a command-and-control (C2) channel. However, further analysis is necessary to determine the source.
Expanding the neighborhood
Understanding that something unknown is executing command and control is a wake-up call. However, just one indicator gives you no additional insight into what to do about the situation.
The next step is to expand the view to include any related research, TTPs, indicators, and meta information that could help you determine not just what's happening but also the likelihood and impact of what already happened and what might happen.
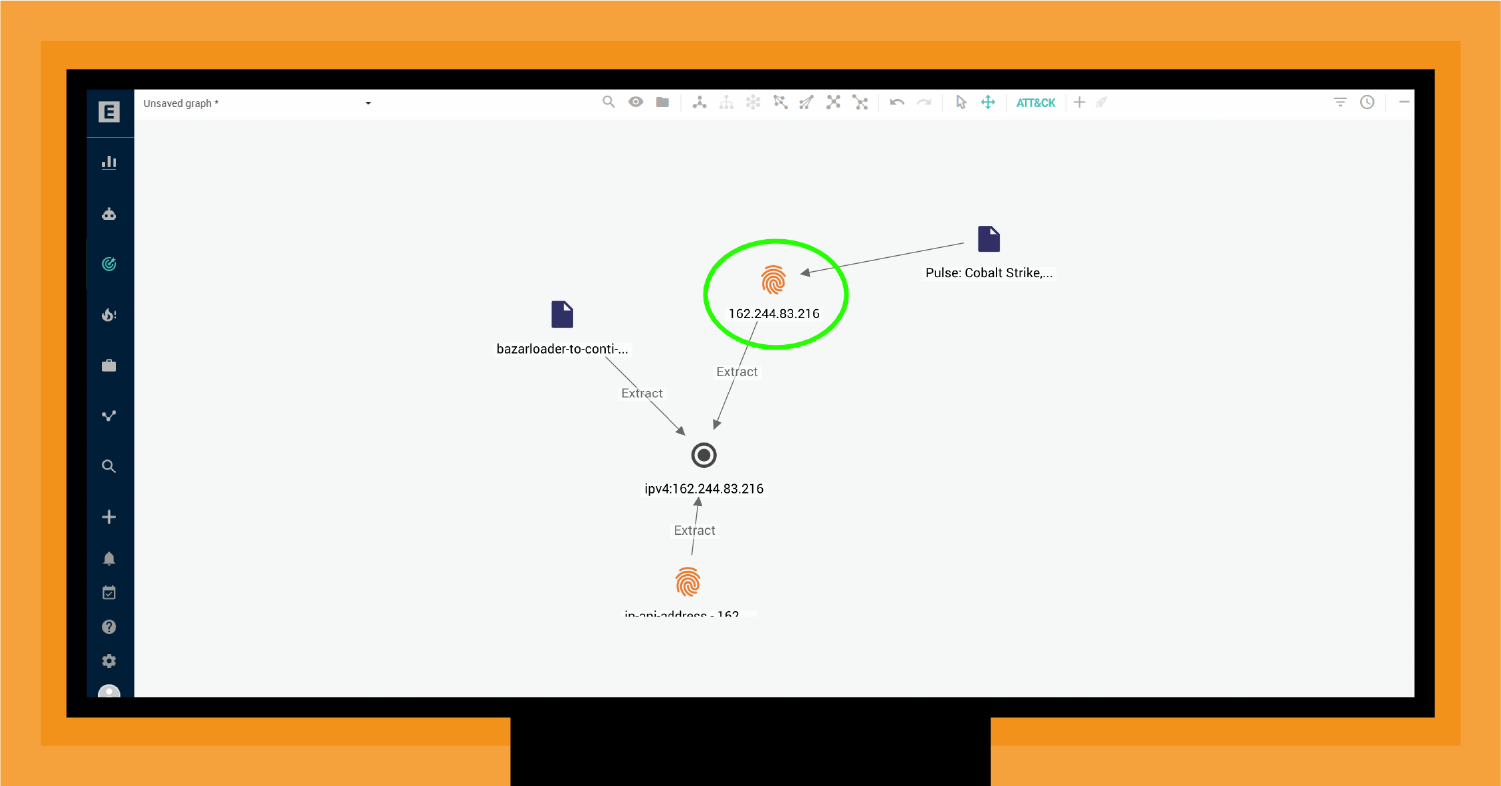
As shown in Figure 2, two significant concerns align with this indicator. First, EclecticIQ Intelligence Center highlights a relationship between this C2 channel and BazarLoader, a notorious initial access broker for ransomware threat actor access. The second and potentially greater concern is that these threat actors typically use CS to run additional discovery tasks using Microsoft utilities. Attackers use these utilities to discover other systems and pivot to further network access.
To understand a specific TTP like CS, the MITRE Cyber Analytics Repository is an excellent source of information.
At this point, where do you go next? Understanding the association of a C2 channel, CS and BazarLoader is valuable, but is it actionable? To make it actionable, you need to understand better how these adversaries can exploit your infrastructure and security controls. This is the perfect time to turn to MITRE ATT&CK.
Going on the ATT&CK
ATT&CK provides a vehicle to align adversary tactics and techniques against your infrastructure and security controls.

ATT&CK presents a matrix of 14 tactics from initial reconnaissance through exfiltration and impact, and a series of techniques and sub-techniques under each tactic.
- Tactics represent the "why" of an ATT&CK technique or sub-technique. A tactic is the adversary's end goal: their raison d'etre. In this case, CS includes several tactics.
- A technique is a single, identifiable behavior that an adversary uses to execute on its end goal.
- A procedure is a specific implementation of a technique.
There is much ground to cover, but as discussed in our last post, ATT&CK is the best summation of adversary tactics and techniques. As we emphasized, with ATT&CK, you focus on approximately 600 techniques rather than tens of thousands of vulnerabilities.
Going “all-in” on MITRE ATT&CK
Before diving into the use of MITRE ATT&CK with EclecticIQ Intelligence Center, it’s worth taking a step back and considering the MITRE ATT&CK approach you need for success. As one of our senior threat researchers says, “With MITRE ATT&CK, it’s only useful if you go all or nothing.” For example, suppose you don’t know how your security controls align to the ATT&CK matrix. In that case, you will have only a minimal ability to assess the potential impact and likelihood of an attack. Similarly, suppose your organization has not bought into the ATT&CK (and the broader TiD) approach and taxonomy. You will spend more time explaining the “how” and “why” of ATT&CK than extracting value from it.
So, before moving forward, it’s critical to commit to using ATT&CK as a framework and your primary means of implementing a TiD.
Mapping the intelligence into ATT&CK
As shown in Figure 2, EclecticIQ Intelligence Center builds a comprehensive view of the relationship between the CS C2 indicator (the suspicious communication your SOC discovered), other indicators and threat actors, and detailed intelligence reports about CS. From these intelligence reports, you can automatically align the information with ATT&CK to help you put this one observation into the broader context of a potentially comprehensive and catastrophic attack.
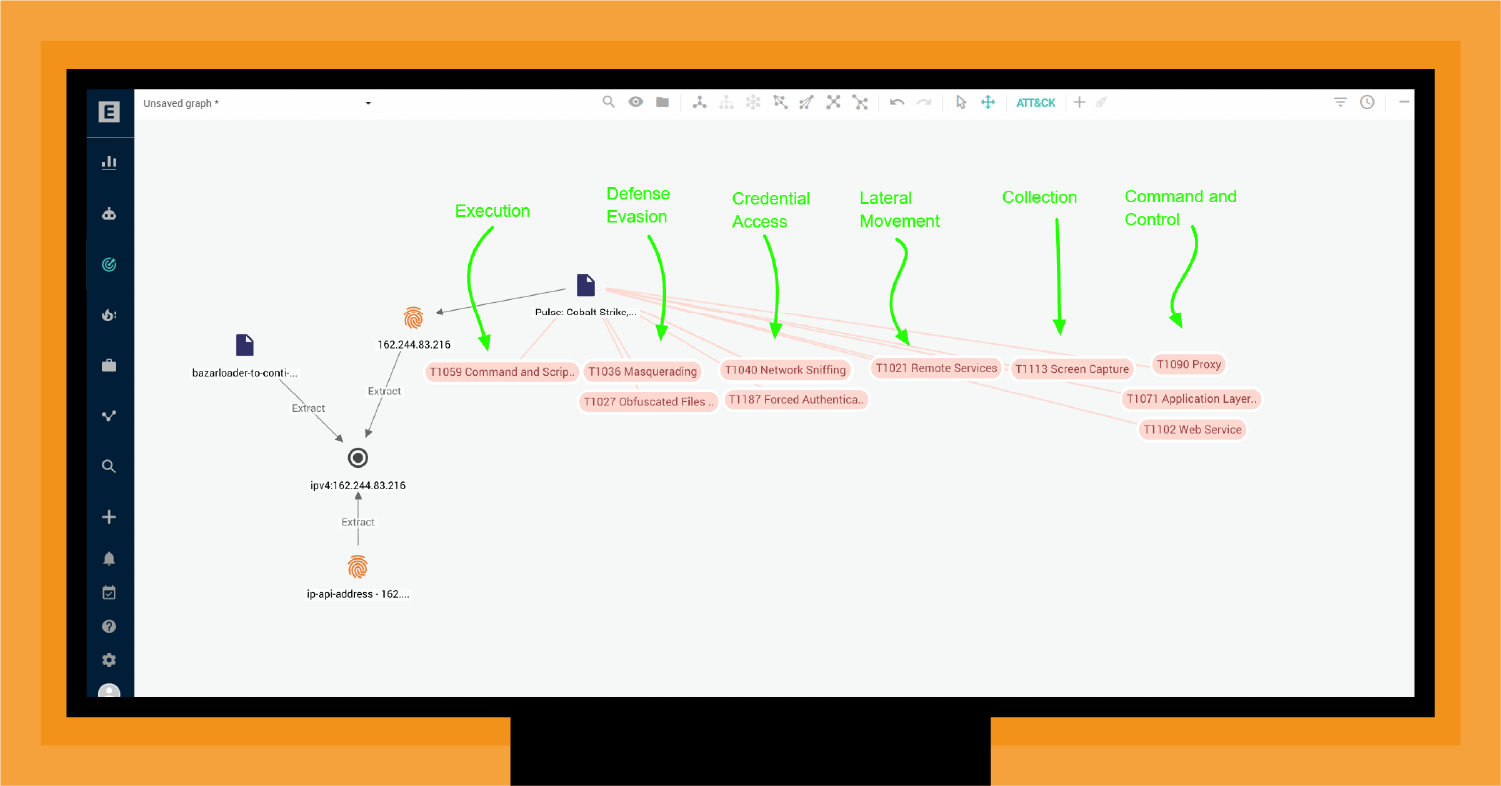
As shown in Figure 4, you have ten different MITRE techniques that align with CS. EclecticIQ Intelligence Center automatically extracts these relationships from the CTI.
Having the alignment of MITRE techniques in the same view as threat actor TTPs and indicators helps to provide additional context about the existence of CS in your infrastructure.
Figure 4 also shows that CS includes TTPs covering much of the Lockheed Martin Kill Chain®, from Execution through Command and Control. Determining where a threat actor is moving within the Kill Chain based on clues from the ATT&CK extraction provides valuable insight into what the adversary is likely to do next, what they have likely already done, and how to end the attack quickly and effectively.
However, it would help to jump to ATT&CK to understand the broader picture.
The integration of EclecticIQ Intelligence Center with the MITRE ATT&CK framework creates equivalent STIX entities in EclecticIQ Intelligence Center. You can use these entities as a common ontology to identify the specific activities of actors and their threat capabilities so you can determine critical overlaps in adversary behavior. For example, you will quickly see if other active TTPs also use CS.
Tracking CS
As shown in Figure 5, ATT&CK maps out 50 techniques and sub-techniques for CS. To highlight these, we weighted these techniques and used color coding. Immediately, you can see that CS is heavy on Defense Evasion (40 techniques), Discovery (29 techniques), Persistence (19 techniques), and Command and Control (16 techniques).
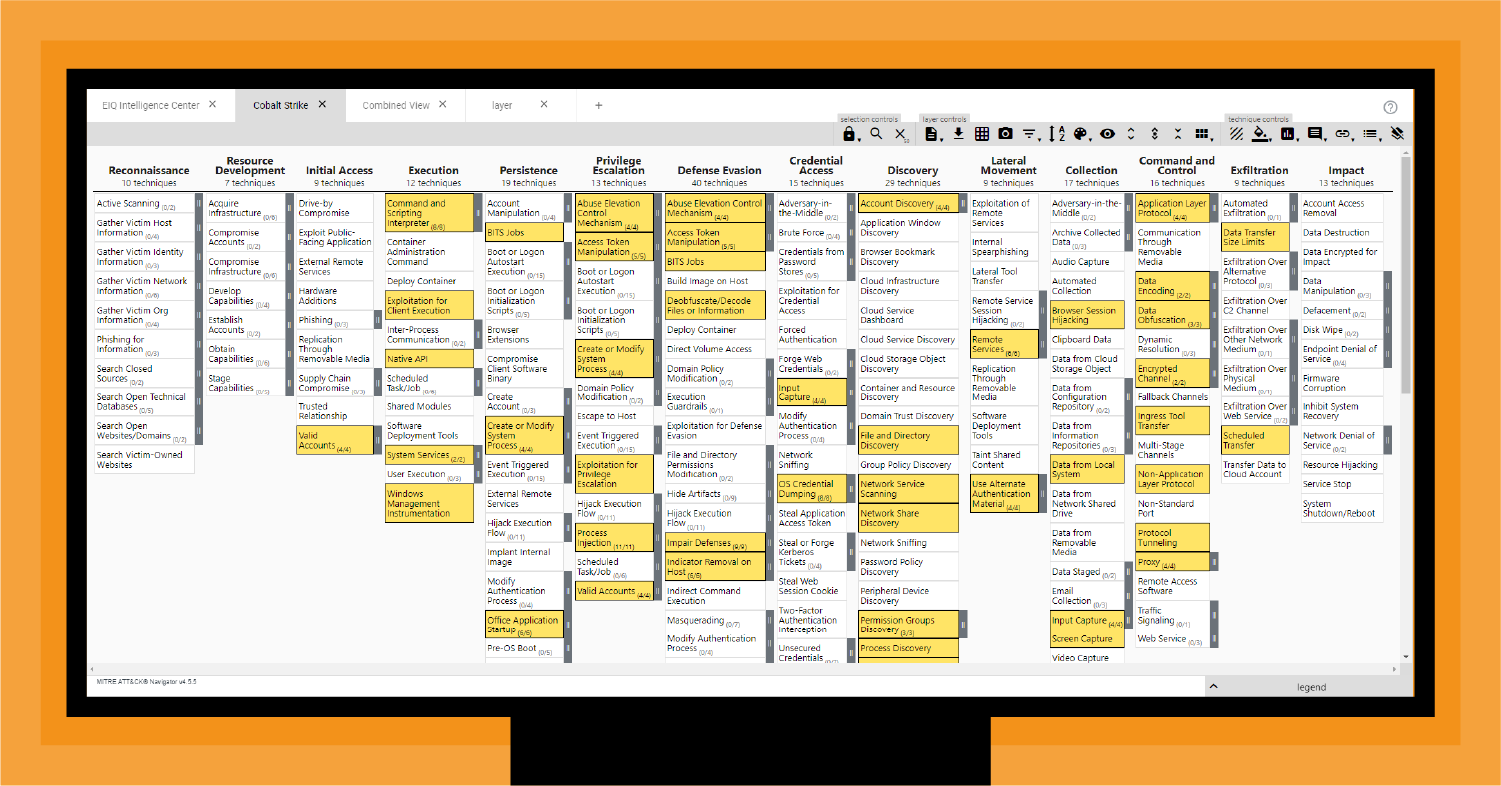
Though the sheer number of techniques doesn't necessarily equate with impact, it certainly shows where the threat adversary is investing development resources: avoiding detection, discovering assets, maintaining residence, and coordinating with outside actors.
Prioritizing your analysis
By aligning the ATT&CK mapping in EclecticIQ Intelligence Center with the ATT&CK knowledge base, you can see the overlap between current active intelligence and the possible TTPs of CS (Figure 6).
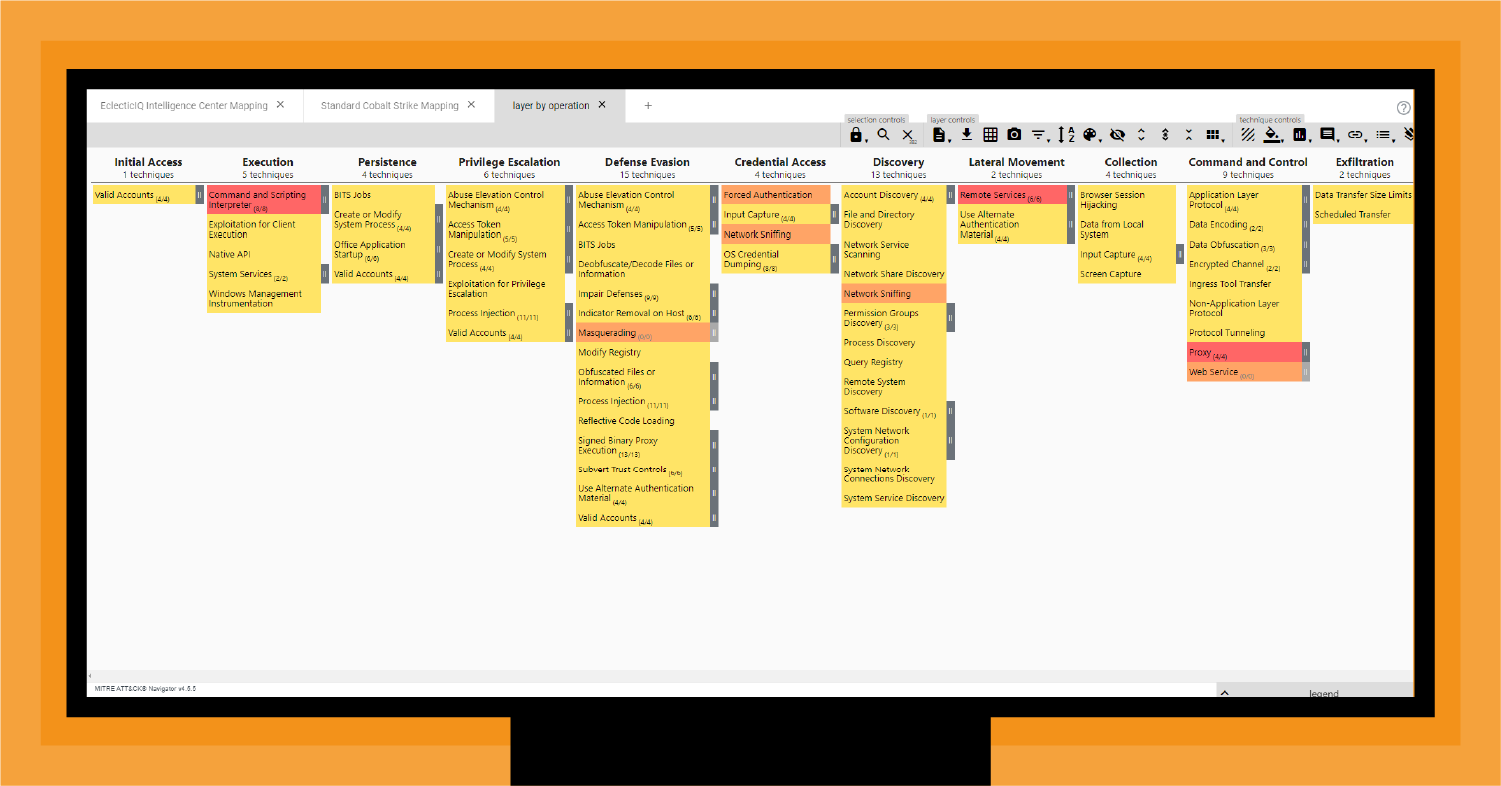
- Red TTPs show a direct overlap between intelligence in EclecticIQ Intelligence Center and the MITRE ATT&CK mapping of CS TTPs. These techniques are the highest priority to investigate, model, and assess against your organization’s defenses because they align with operational intelligence in the EclecticIQ Intelligence Center knowledge base. In other words, these TTPs align with what you know is happening.
- Orange TTPs are in EclecticIQ Intelligence Center but do not directly align with MITRE ATT&CK CS TTPs. For example, T1036 Masquerading is a technique that does not always fit with CS. These techniques are a second priority because they may indicate a new variant of CS is active or you are dealing with multiple threat actors deploying TTPs that overlap with CS. As discussed below, EclecticIQ Intelligence Center is aligning CS and Conti ransomware as a service (RaaS), which expands the possible TTPs in play in your infrastructure. These TTPs align with what might be happening.
- Yellow TTPs are part of ATT&CK CS mapping but do not appear in EclecticIQ Intelligence Center— yet. As part of a TiD approach, you should assess your ability to defend against these TTPs as a preemptive step for the next CS-related attack. These TTPs align with what could be happening next.
What to do next?
By aligning the CS tactics and techniques with the graph neighborhood in EclecticIQ Intelligence Center, you now have a larger view of what’s going on beyond a single suspect C&C channel. Your first action should be blocking the channel and extinguishing the immediate threat. To help with this, you can generate YARA rules directly from EclecticIQ Intelligence Center to pass to your firewall and IDS/IPS.
However, this is not the end of the investigation. It is just the beginning. All you’ve done is block one C2 channel that you know about. There may be other CS beacons that the adversary has already dropped, or the attacker may have moved beyond CS by loading additional malware while you were busy shutting down this one C2 channel.
Attaining three essential views
As a network defender, you need to look past the obvious and determine what else is happening. Essentially, you need a much more extensive viewpoint, and this alignment with ATT&CK gives you that bigger picture. It allows you to establish three fundamental views:
Looking back
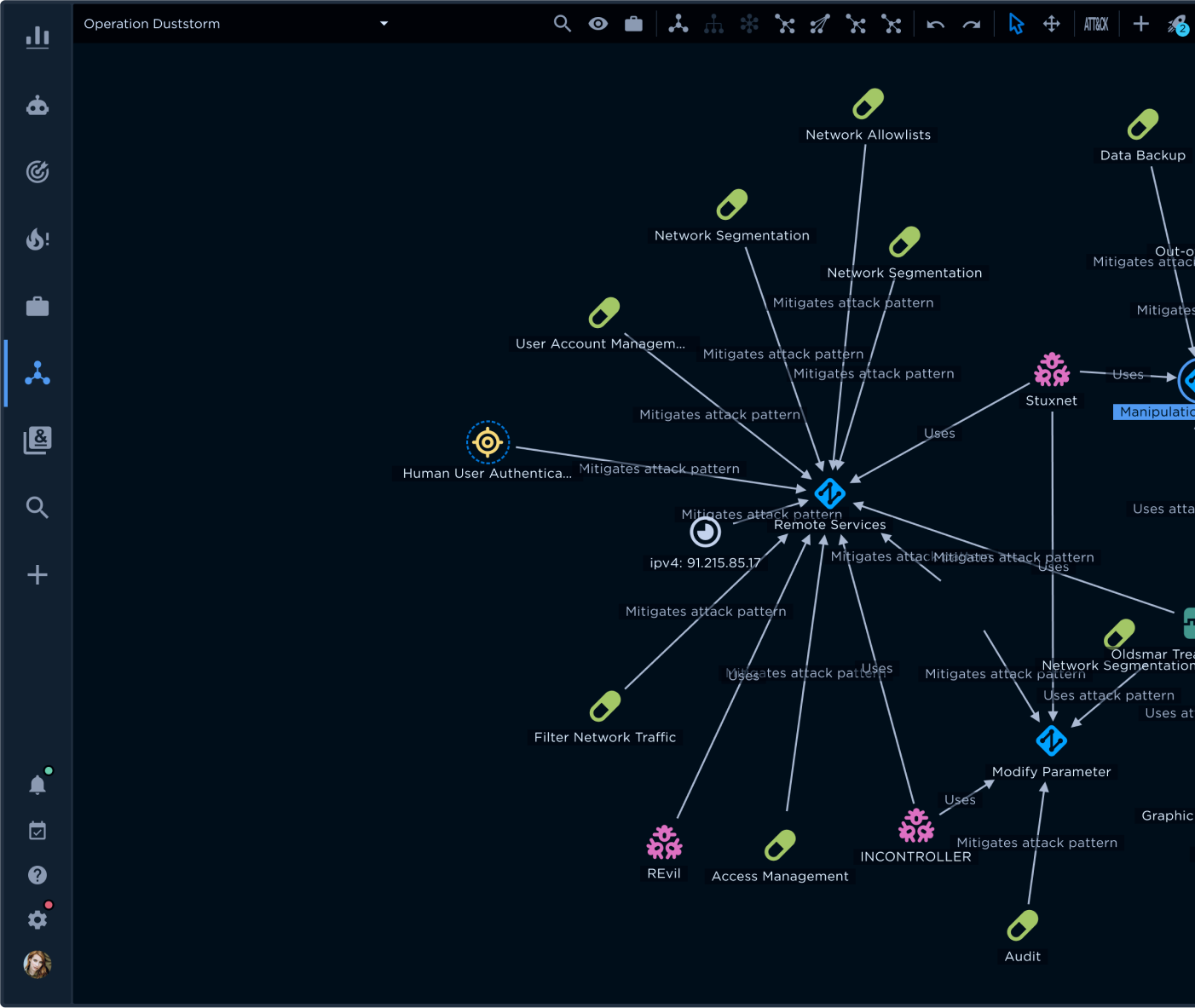
It would help if you determined how the adversary was able to establish this C&C channel. With ATT&CK, you can use upstream mapping to focus on the potential defenses the adversary compromised or the defenses that were not there in the first place. For example, lateral movement is a core tactic of CS. Understanding the techniques adversaries may use is essential to shore up your defenses.
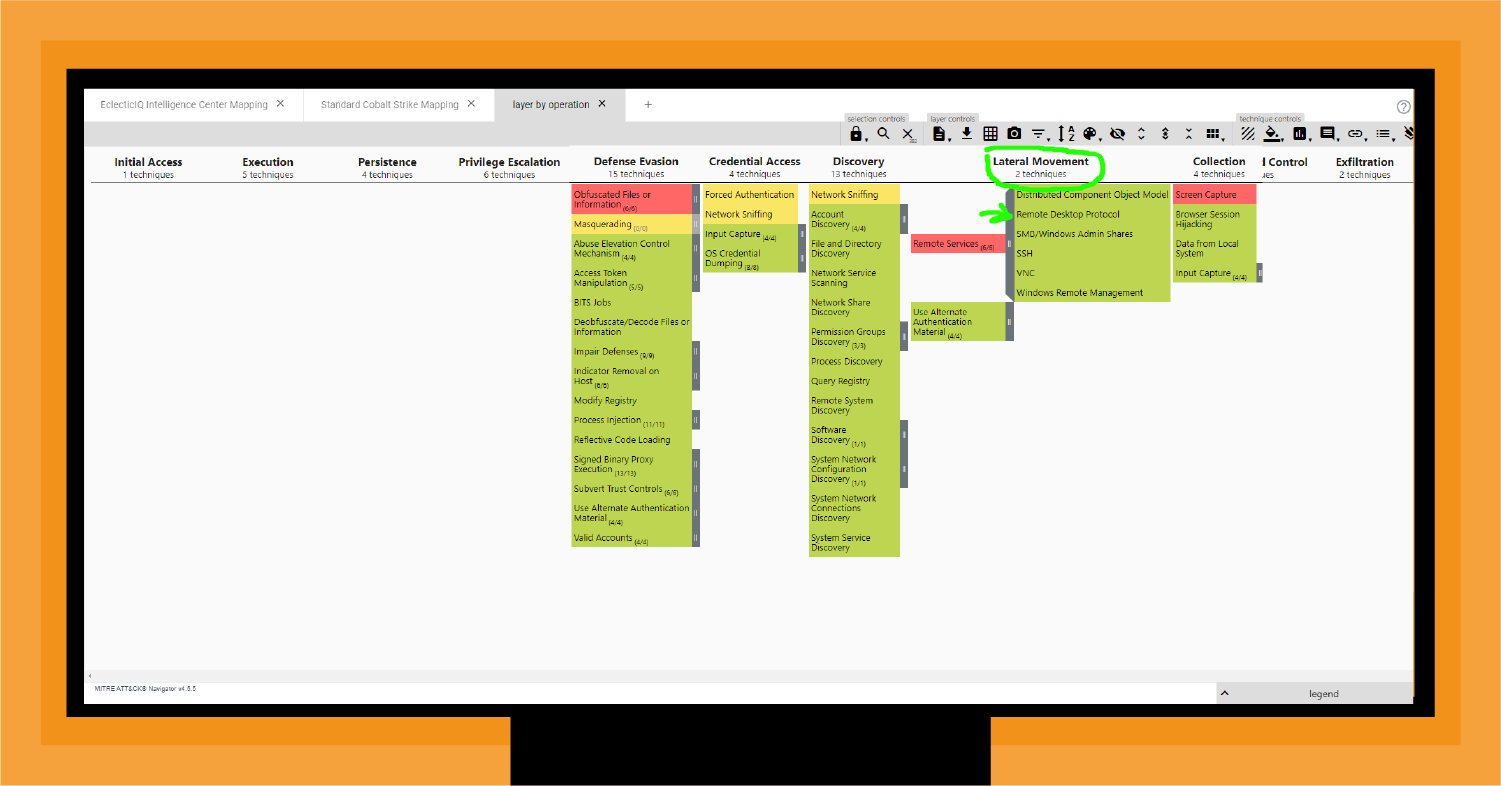
As shown in Figure 7, Remote Desktop Protocol (RDP) is a sub-technique for remote services. We highlight this since RDP is a favorite target whose use has become more prevalent with the shift to work from home, often involving endpoints that no longer had corporate firewalls blocking RDP access.
Looking forward
This analysis helps you determine how you will fare with the next variants of CS. We see variants arise every three to six months, so you need to project how your infrastructure will stand up to them. As we discuss in “Shifting from What to How to Get Ahead of the Threat,” the key is shifting your focus from one IOC to the TTPs behind that IOC.
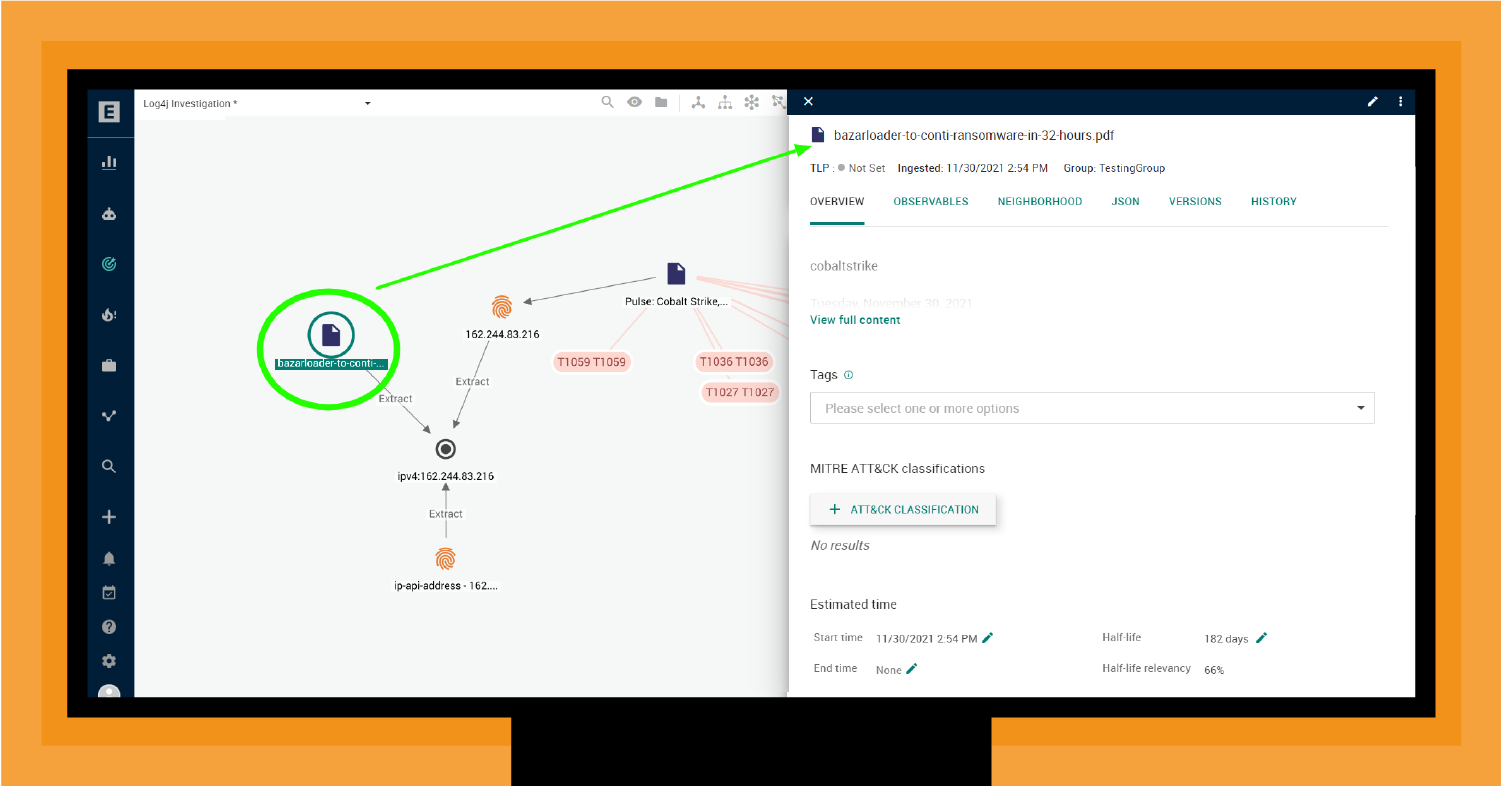
As shown in the EclecticIQ graph (Figure 8), there is a known relationship between the use of CS and the Conti RaaS. As discussed in “Operationalize Your Threat Intelligence in Four Moves,” ENISA found an increasing focus on RaaS business models in its “ENISA Threat Landscape 2021” report.
By mapping the TTPs of CS and aligning this map with additional intelligence (e.g., Conti RaaS), you can better prepare for both future variants of CS and related TTPs (e.g., Conti delivering BazarLoader DLL).
Looking outward
This hypothetical use of CS was part of a broader APT29 attack on the supply chain. Threat actors like APT29 are stealthy, often detected only by tracking adversary activity over time. For example, one of our clients tracks adversary activity over a rolling six-month window. They create a MITRE ATT&CK heat map that aligns multiple incident response analyses (like this one).
With this ATT&CK heat map, they can see broad trends that help them better detect actors like APT29 and align their defenses accordingly. For example, by mapping multiple adversarial tactics and techniques that target financial services organizations, they immediately noted the rising use of ransomware that uses the primary Initial Access technique of phishing (T1566). Digging deeper, they could target attachments (T1566.001) as the primary vector. With this knowledge, they could better model this adversary behavior and run purple team exercises to test their SPAM filters, firewalls, and IDS/IPS controls.
This approach helps our clients – and you – get better over time. This investigation makes the entire team better prepared to address the next use of CS or a similar type of malware. A core tenet of a TiD is incrementally improving your defense over time.
Though this post started by focusing on an IOC (a C2 channel), the discussion quickly moved to TTPs. Indeed, this shift is essential for getting ahead of the attack, reducing attackers’ dwell time in your network, and widening the time between breaches. As we discuss in “Shifting from What to How to Get Ahead of the Threat,” there is great value in moving quickly from IOCs to TTPs by focusing on how rather than on what.
Where do I go from here?
MITRE ATT&CK empowers you to map TTPs back to your security systems and processes to shore up your detection and response capabilities. In summary, we recommend the following steps to use MITRE ATT&CK to map and track adversary TTPs:
- Understand ATT&CK, how it works, and what it provides. Excellent sources of information are the MITRE ATT&CK Navigator and MITRE Center for Threat Informed Defense.
- Research target behaviors by leveraging MITRE ATT&CK and MITRE CAR. For example, if you know that an adversary uses T1064 (scripting), you need to understand why and where scripting affects your infrastructure. Scripting plays a substantial role in phishing as a means to deliver malicious payloads. Because of this, you will want to assess your ability to immediately detect any unauthorized code running on perimeter systems exposed to the internet. The key to conducting this research is to have a potent, knowledgeable threat intel analyst team working for you to put the pieces together quickly and make new connections from the data.
- Translate the target behaviors to specific tactics.
- Determine the techniques the adversary uses to accomplish the tactics. The key here is uniting the ATT&CK library with what you are seeing. Your threat intelligence management platform is instrumental in providing a dashboard for this alignment. Your ability to detect and respond depends on having actionable data on what is happening in an attack.
- Use mapping and prioritization to close the loop on the threat and perform additional hunting activities to monitor any related activity effectively.