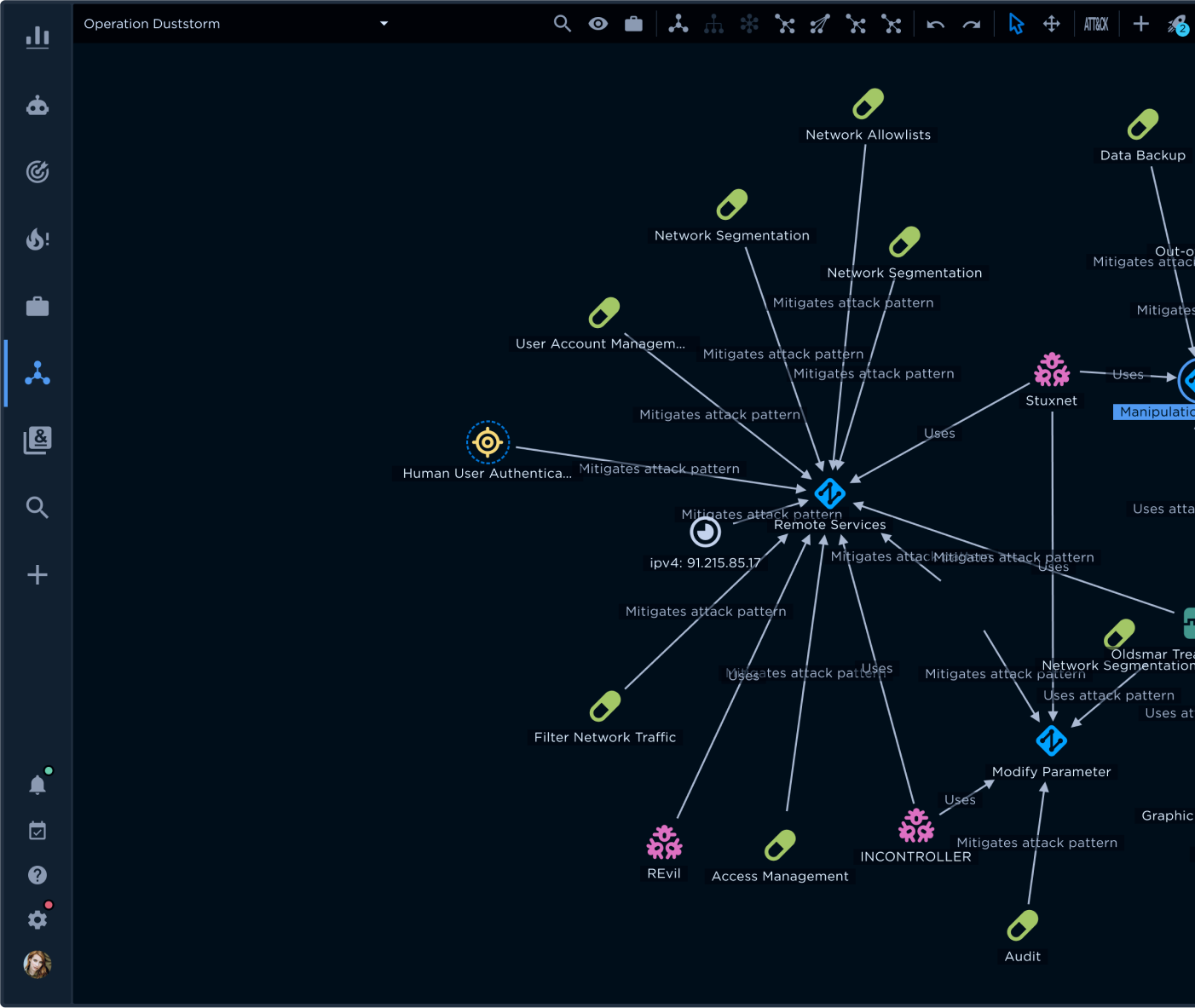
Cyber threat intelligence (CTI) as a formal practice is gaining traction. In fact, 47 percent of participants in a recent SANS survey state that they have dedicated, in-house CTI teams.1 The holy grail for these teams is operationalizing their CTI to benefit peer groups and organizational leadership. Operationalized CTI helps executives define and shore up the organization’s cyber posture. It helps Security Operations Center (SOC), Incident Response (IR), and other front-line teams to hunt down, identify, and respond to threats faster.

So, how do you operationalize threat intelligence? Approaches vary greatly. CTI can fuel your threat hunting program and your endpoint and extended detection and response (EDR/XDR) efforts to find undetected adversarial activity. Or, CTI can drive security orchestration and response (SOAR) so you can accelerate and automate incident response.
Regardless of the approach, you’ll face four significant challenges in operationalizing CTI:
1. Threat adversaries are getting better at what they do and more successful at overcoming new defense tactics
As threat actors become more adept, operationalizing threat intelligence becomes more challenging because it is increasingly difficult to detect attacks. To underscore this point, in ENISA’s recent Threat Landscape 2021 report, ransomware moved to the head of the line as “the prime threat for 2020-2021.”2 Coinciding with this trend, ENISA found, “Malware developers keep finding ways to make reverse engineering and dynamic analysis harder.” Plus, threat actors are not only getting smarter, but they are getting more businesslike in delivering their services. ENISA found an increasing focus on Ransomware as a Service (RaaS) models.
2. A rapidly expanding attack surface makes your organization more vulnerable
An expanding digital footprint that includes cloud and mobile connectivity increases the scope and scale of the CTI necessary to cover the attack surface. Work from home (WFH) initiatives prompted by COVID-19 have accelerated the expansion of the attack surface, as employees around the globe use their personal devices to access critical information. As ENISA states, “Cybersecurity threats related to the pandemic and exploiting the ‘new normal’ are becoming mainstream.”3 You may have seen a rise in the number of cyberattacks targeting your workers in home offices, via routers and Internet of Things (IOT) devices.
However, the challenge goes beyond WFH. ENISA also found that cybercrime attacks increasingly target critical infrastructure, the supply chain, and container environments to breach the DevOps environment.
3. A shortage of skilled IT specialists results in siloed operations and poor coordination, leaving gaps in your coverage
Siloed operations create gaps in cyber coverage, leading to significant blind spots. Operationalizing CTI that has holes in coverage is, at best, inconsistent. At worst, it gives you a false sense of security while leaving swaths of infrastructure without oversight. Silos are a side effect of the critical cyber skills shortage, which exerts continual pressure to create segregated and specialized teams, use third parties, and leverage technology to make up for lean staffing. The result may be an overabundance of point solutions, over-reliance on a brittle supply chain of, and overdependence on specialized, segregated operations.
4. Information overload makes it harder to identify advanced TTPs
As the scale and sophistication of attacks increase, your security teams are undoubtedly “drinking from the firehose” -- under enormous pressure to keep up with indicators of compromise (IOCs) and SIEM alerts. It’s a struggle to separate valuable data from noise, which is essential for operationalizing CTI so you can improve detection, hunting, and response. For example, new threats that generate alerts often turn out to be old tricks showing up in new packaging. While ENISA found the danger of malware declining in relation to other threats, at the same time there was an increase in threat actors applying new or uncommon programming languages to port their code. You may have to face the fact that your tools aren’t powerful enough to isolate actionable patterns or lack the capabilities necessary to operationalize CTI.
A CTI program requires actionable intelligence
There’s a common theme to these four challenges: the need for actionable intelligence. Without actionable CTI, it is impossible to get ahead of emerging adversary tactics, quickly cover the entire threat landscape, shore up gaps in coverage, and help your security team detect stealthy TTPs.
Unfortunately, your CTI program may not be producing actionable intelligence. Instead, you may receive information lacking context and value. Worst case, this information flow is simply a noisy distraction.
One of our global banking clients tells us, “Determining that anonymous actors are targeting the financial sector is important, but it’s not directional. Determining that actors are looking for information or specific targets like my bank is something I can operationalize.” In other words, he expects the CTI he operationalizes to be actionable. Case in point: respondents in a 2021 Ponemon study indicated they did not stop 40 percent of cyberattacks they otherwise could have contained had they had timely and actionable intelligence.4
How can you deliver actionable CTI?
As we will be discussing in a series of related blog posts, an actionable CTI program requires you to take the following steps:
 1. Empower your defenders by shifting the focus from IOCs to TTPs
1. Empower your defenders by shifting the focus from IOCs to TTPs
This shift is essential for identifying more-sophisticated attacks and old tactics disguised as something new. Raw indicators are insufficient to detect an attack from a threat actor using adjusted capabilities or modified malware. Instead, your team must look at the framework and methodologies behind attacks (e.g., MITRE ATT&CK) to build actionable intelligence that keeps pace with TTPs. Plus, until your team can sidestep the IOC firehose, they will never get ahead of the threat. The quality and coverage of your threat intelligence feeds become paramount as you refocus on processing data into information and building intelligence.
2. Simplify the security stack and close cybersecurity coverage gaps
Focus on interoperability by leveraging open standards such as STIX and MITRE ATT&CK to create a common communication baseline. A word of caution: many security controls do not support these open standards. Because of this, you need an extensible API that provides seamless integration with other security platforms (e.g., SIEM, SOAR, EDR/XDR) and any non-standard services, devices, and applications.
3. Accelerate collaboration among security teams
Successful security and risk management is a team sport—the more collaborative the environment, the better the opportunity to develop and operationalize actionable CTI. Encouraging collaboration requires a threat intelligence platform that allows you to share a common view of the threat landscape with context for operational teams on what is happening in your organization and across your supply chain.
4. Align your detection and response with robust intelligence requirements
Your CTI will become more actionable when you establish vital intelligence requirements that reflect the needs of your organizational leadership, risk management, incident response, and vulnerability management teams. These requirements determine what types of adversaries to look for and the resources that they target. Prioritizing threats is critical to developing a solid runbook for responding to an incident, should one occur, and minimizing the chances of an attack in the first place.
Conclusion
Following these four steps will enable you to position your CTI program to operationalize actionable CTI. Of course, these are significant steps to take. In our next post, we’ll discuss how EclecticIQ Intelligence Center can help you complete them so you can operationalize threat intelligence as you develop and deliver actionable CTI.
Footnotes
- “SANS 2022 Cyber Threat Intelligence Survey,” SANS, 2022. Page 5.
- “ENISA Threat Landscape 2021,” ENISA, October 2021. Page 4.
- “ENISA Threat Landscape 2021,” ENISA, October 2021. Page 7.
-
“The State of Threat Feed Effectiveness in the United States and United Kingdom,” Ponemon Institute Research Report, March 2021.