What is STIX and TAXII?
The industry standards for Cyber Threat Intelligence.
STIX
STIX (Structured Threat Information eXpression) is a standardized language which has been developed by MITRE in a collaborative way in order to represent structured information about cyber threats. It has been developed so it can be shared, stored, and otherwise used in a consistent manner that facilitates automation and human assisted analysis.
TAXII
TAXII (Trusted Automated eXchange of Indicator Information) is a collection of services and message exchanges to enable the sharing of information about cyber threats across product, service and organizational boundaries. It is a transport vehicle for STIX structured threat information and key enabler to widespread exchange.
Why is it important?
STIX and TAXII allow transportation of threat information among IT security and intelligence technologies. Re-aligning IT security efforts based on real-time information exchanges between government, commercial suppliers, non-profit efforts and industry partners. One organization’s reactive, is the other’s proactive.
STIX and TAXII are open community efforts sponsored by the U.S. Department of Homeland Security are heavily supported by MITRE corporation. Enjoying global adoption, the industry will need to continue to work together and build upon this platform to make STIX and TAXII standards we continue to rely on.
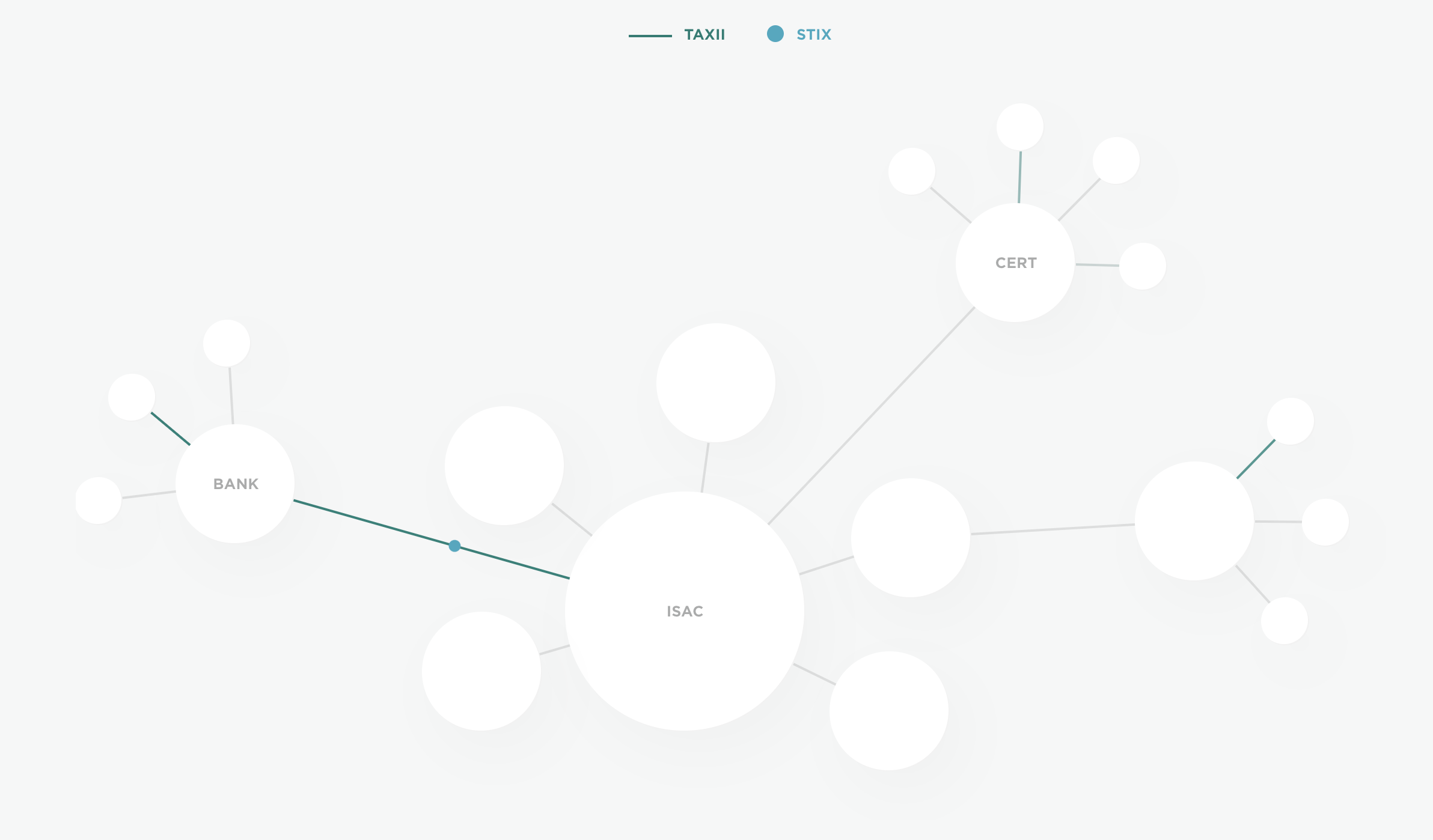
The ecosystem
Get started
-
1. Read About STIX and TAXII
MITRE and the community have consolidated their documentation on Github. Find STIX documentation here and TAXII documentation here.
-
3. Transform your Intelligence / Indicators
Learn more about how to represent information in STIX, subscribe to the mailinglist or contact us at stixtaxii@eclecticiq.com.
-
4. Lift off!
Congratulations! You’re now part of the STIX and TAXII community. Talk to you on the mailing lists or contact us at stixtaxii@eclecticiq.com if you need any further assistance.
STIX and TAXII in action
Resources
-
STIX 2.1
Explore the full STIX documentation here and get started with structured threat intelligence today.
-
Awesome libraries
A python library and java bindings for parsing, manipulating, and generating STIX content.
-
TAXII collection
Our public TAXII collection contains all structured data that is included with our Analyst Prompt publications. Please refer to our support page for guidance.