For Collaboration & Dissemination
Enable SOC teams to better operationalize threat intelligence for more effective and efficient incident response with our range of analyst-centric management products and services.
Challenge
As a National Cybersecurity Center (NCSC) or a National Computer Emergency Response Team (National CERT), your success resides in your teams’ ability to meet the following objectives:
- Develop actionable intelligence by consolidating vast amounts of threat data and collaborating internally to process this data quickly.
- Empower constituents and collaborative organizations by efficiently disseminating intelligence for human and machine consumption.
- Validate and quickly respond to active threats by feeding intelligence into national sensor networks.
- Achieve early warning of active threats by creating collaborative communities to share expertise and intelligence.
For many organizations, achieving these goals is nearly impossible for two key reasons. First, your in-house tools (often open source and homegrown) lack rich collaboration, granular analyst workflows, effective dissemination capabilities, and sensor network integrations to achieve the first three objectives. Second, these tools lack the controls necessary to protect constituent and collaborative community data confidentiality and privacy, meaning that you can never accomplish the fourth goal.
Solution
Overcoming these challenges requires implementing a threat intelligence collaboration and dissemination solution that does the following:
-
Implement a threat intelligence solution
That lets your staff optimize, prioritize, and organize vast amounts of structured and unstructured threat data automatically.
Read moreThat lets your staff optimize, prioritize, and organize vast amounts of structured and unstructured threat data automatically.
-
Stand up a shared collaborative workspace
That supports collaboration with advanced role-based access controls (RBAC) to protect the confidentiality of data that your teams share ... Read more
That supports collaboration with advanced role-based access controls (RBAC) to protect the confidentiality of data that your teams share internally.
-
Implement a solution
That disseminates high-quality human-readable reports to stakeholders and machine-readable feeds for constituent security controls to ... Read more
That disseminates high-quality human-readable reports to stakeholders and machine-readable feeds for constituent security controls to improve response.
-
Establish analyst workflows
That allow your analysts and threat hunting teams to quickly establish and prioritize relevant intelligence and feed this intelligence ... Read more
That allow your analysts and threat hunting teams to quickly establish and prioritize relevant intelligence and feed this intelligence into national sensor networks to verify and respond to active threats.
-
Implement bi-directional sharing
Of intelligence with the data privacy and confidentiality controls to protect collaborative members’ data.
Read moreOf intelligence with the data privacy and confidentiality controls to protect collaborative members’ data.
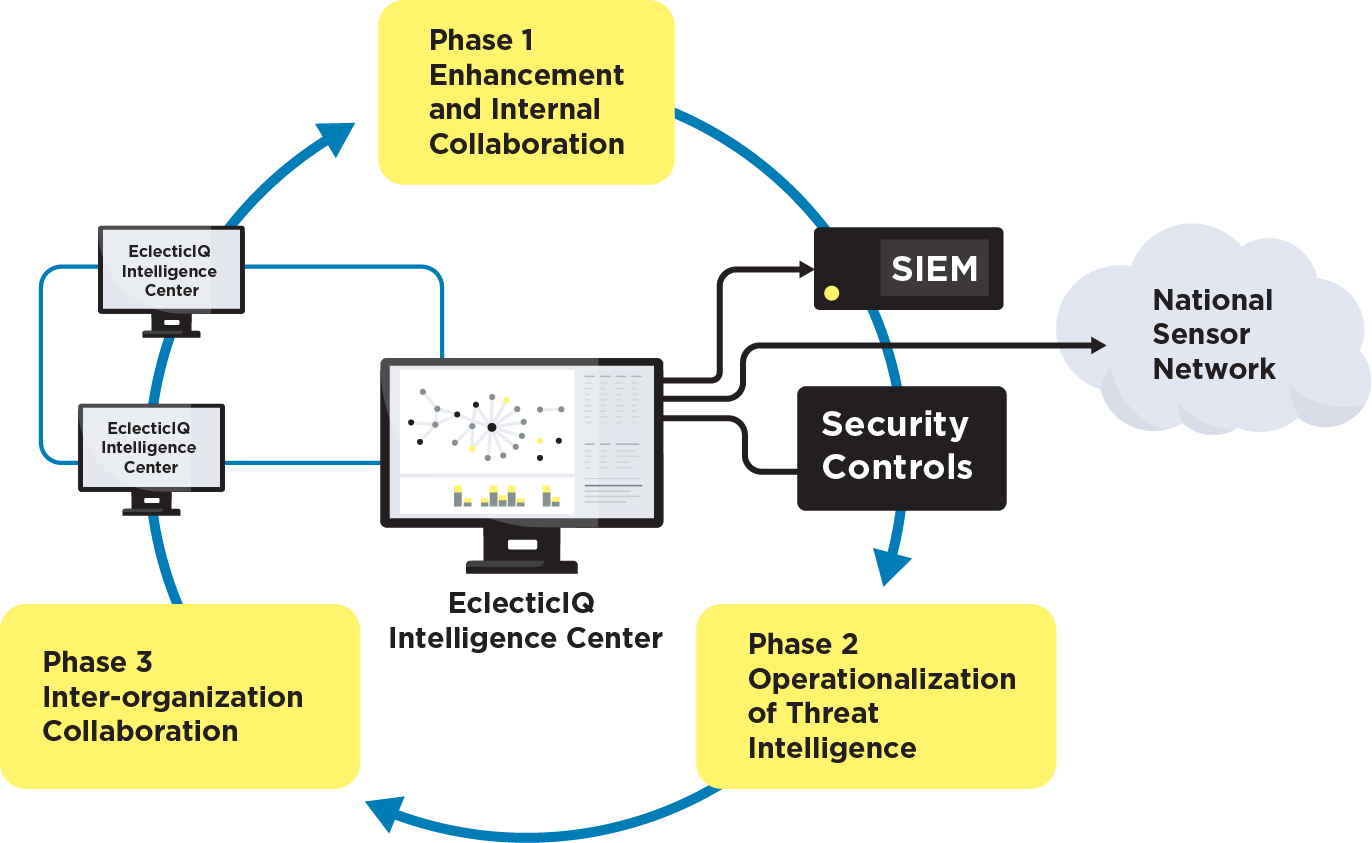
Approach
As described in EclecticIQ Empowers a National CERT’s Collaborative Threat Intelligence Sharing Community case study, EclecticIQ’s approach is pragmatic and proven. We work with NCSCs and National CERTS to implement a three-phase strategy for dissemination and collaboration:
Phase 1 – Enhancement and Internal Collaboration
During this phase, your team uses EclecticIQ Intelligence Center to enhance threat data through analysis and enrichment and automatically disseminate human- and machine-readable intelligence using STIX/TAXII and community-specific protocols. Your team starts working together better through collaborative workspaces to analyze threats, track campaigns and cases, prioritize intelligence, and manage alerts.
Phase 2 – Operationalization of Threat Intelligence
This phase enhances your threat data prioritization and implementing analyst workflows for disseminating data to national sensor networks to improve the organization’s threat response. EclecticIQ Intelligence Center powers deep threat investigations with advanced search queries, intuitive graphical link analysis, and support for leading CTI frameworks, standards, and libraries that help your analysts align to MITRE ATT&CK and identify the Tactics, Techniques, and Procedures (TTPs) of sophisticated threat actors.
Phase 3 – Inter-organization Collaboration
During this final phase, your team takes advantage of EclecticIQ Intelligence Center’s flexible architecture to support different collaboration models (e.g., hierarchical, flat, hub-and-spoke, and hybrid). With the correct model, your team can leverage the unique threat knowledge of other organizations to quickly and automatically collaborate and disseminate critical threat intelligence to achieve an early warning system for active threats.
BENEFITS
Empower your team:
- Boost your CTI team’s productivity by optimizing, prioritizing, and organizing vast amounts of structured and unstructured threat data automatically.
- Protect shared data with collaboration that supports advanced RBAC.
Improve dissemination and response:
- Deliver more actionable intelligence by disseminating high-quality human-readable reports to stakeholders and machine-readable feeds for constituent security controls.
- Facilitate faster response with analyst workflows that allow your analysts and threat hunting teams to quickly establish and prioritize relevant intelligence and feed this intelligence into national sensor networks to verify and respond to active threats.
Establish inter-organization collaboration for early warning:
- Achieve early warning while protecting collaborative members’ data by implementing bi-directional sharing of intelligence with data privacy and confidentiality controls.
Related Packages, Products & Services
EclecticIQ TIP for CTI
Power your CTI practice with our analyst-centric threat intelligence platform.
EclecticIQ Intelligence Center
Automate threat intelligence management and analyst workflows with the analyst-centric Threat Intelligence Platform.
EclecticIQ Curated Feeds
Track primary threats with curated threat data feeds optimized for EclecticIQ intelligence center.
Threat Intelligence Consultants
Supercharge your threat intelligence operations with expert guidance.
Platform Overview
Discover our unique approach to Intelligence, Automation and Collaboration.
Intelligence at the core™
Stay ahead of rapidly evolving threats and outmaneuver your adversaries.
EclecticIQ is trusted by the best in cybersecurity




