An effective CTI practice must align the information needs of your stakeholders with the reality of the threat landscape while remaining within ever-present business constraints on resources and budgets. In this environment, your critical success factors are: (1) building a CTI practice that focuses on internal needs; (2) aligning with key stakeholders; (3) adopting metrics that track progress; (4) optimizing human resources; (5) implementing processes that follow industry best practices; and (6) adopting technologies that are fit for purpose.
Before getting into what it takes to meet your stakeholders' information needs, let's focus on threat intelligence and its potential impact on your organization.
What is threat intelligence?
At its core, intelligence is about reducing uncertainty. When the uncertainty involves threats to business objectives, intelligence decreases business risks. CTI, specifically, reduces uncertainty when dealing with threats such as electronic crime, hacktivism, terrorism, and espionage.
Reducing this uncertainty and managing these cyber risks require information that cyber adversaries prefer to conceal. Intelligence analysts must uncover this concealed information using direct and indirect means of collecting and analyzing available data. During this process, they establish facts and then develop precise, reliable, and valid inferences for decision making. Their resulting conclusions and predictions benefit your operational planning for security operations, incident response, vulnerability management, and risk management, as well as board-level decision making.
A CTI practice follows traditional intelligence processes to focus on operational, tactical, and strategic responses to cyber threats.
A common way to describe these processes is the management of "knowns" and "unknowns" (See Figure 1). The most dangerous are the "unknown unknown" threats we do not know about or understand. Accordingly, the first step in intelligence processing is to discover the existence of threats – the "known unknowns" – and subsequently work to understand them better as "known knowns." Only after you have a "known known" can you take appropriate action. This continuous process of threat identification, understanding, and action is a good high-level description of the CTI practice.
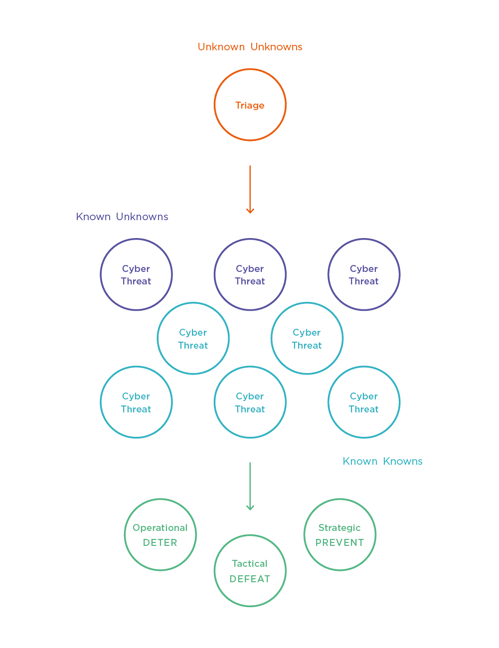
Figure 1 - Known and unknown cyber threats
On a practical level, your CTI team must constantly evaluate the changing threat landscape to update your organization on the most effective way to counter emerging threats, given the available resources.
Yes, you need a CTI maturity model
Ultimately, the role of your CTI organization is to implement processes that leverage CTI to defeat present attacks, deter ongoing actions, and prevent future attacks.
Building these processes is a complex undertaking that takes considerable time and money. To justify this investment, you must be able to determine if you are getting the best outcome from your CTI analyst team, if their intelligence is actionable, and if you are satisfying your stakeholders. As we discuss in this paper, you can't make these determinations without highly mature processes.
Cue the maturity model discussion! Yes, mentioning maturity in an IT context is impossible without jumping into a maturity model discussion, for good reasons:
- Maturity models establish a common language for discussing CTI processes.
- They provide a means to benchmark your CTI team's performance and its impact on your organization.
- They act as a catalyst for change by pointing out your strengths and weaknesses.
Adopting a maturity model allows you and your team to step aside from the daily firefighting associated with CTI operations to assess current capabilities and develop a path to improving these capabilities over time. With the right approach, you will be able to answer the following critical questions:
- Am I getting the best result from my CTI analyst team?
- Am I sending the correct information to the right people and controls at the right time?
- Are all my stakeholders empowered by the intelligence (or information) they are receiving?
- Is my CTI team helping the organization to prevent or pre-empt a breach
OK, so I’m sold on the idea of a maturity model. What now? In our next blog, we introduce you to an innovative and unique CTI maturity model.