In our previous post we highlighted the importance of early warning to cyber resilience. Early warning is all about anticipating attacks. The better your organization can anticipate, the better positioned you will be to respond, withstand, and recover from an attack. Given early enough warning, you can even prevent attacks.
Unfortunately, very few organizations have sufficient internal resources and external inputs to develop a complete attack picture in time to anticipate an attack. This is where early warning is so helpful: it supplies essential information to fill in the gaps in your attack picture.
Filling in these gaps requires threat sharing and collaboration, both within your organization and with peer organizations. Although you may feel this is the responsibility of a national cybersecurity center (NCSC), sharing and collaboration are rapidly becoming every organization's job. An expanding attack surface and increasing dependence on the supply chain mean that your security perimeter no longer ends at your corporate data center. For this reason, you must act like an NCSC or information sharing and analysis center (ISAC) to provide early warning for your organization and its supply chain.
Anticipating attacks requires collaboration
So, how do you become more like an NSCS or ISAC to better protect your organization and its supply chain? You need to implement an early warning protocol for your organization. We recommend a three-step protocol: implementing a scalable and extensible platform, establishing shared, secure workspaces, and aligning all stakeholders for a coordinated response.
To provide context for this discussion, we'll focus on SolarWinds, one of the gravest attacks against the supply chain to date. Though the original campaign has concluded, it's a relevant case study because we believe SolarWinds is a playbook for future sophisticated attacks.
By establishing early warning against SolarWinds-type attacks, you will position your organization and supply chain to address new attacks that follow similar game plans.
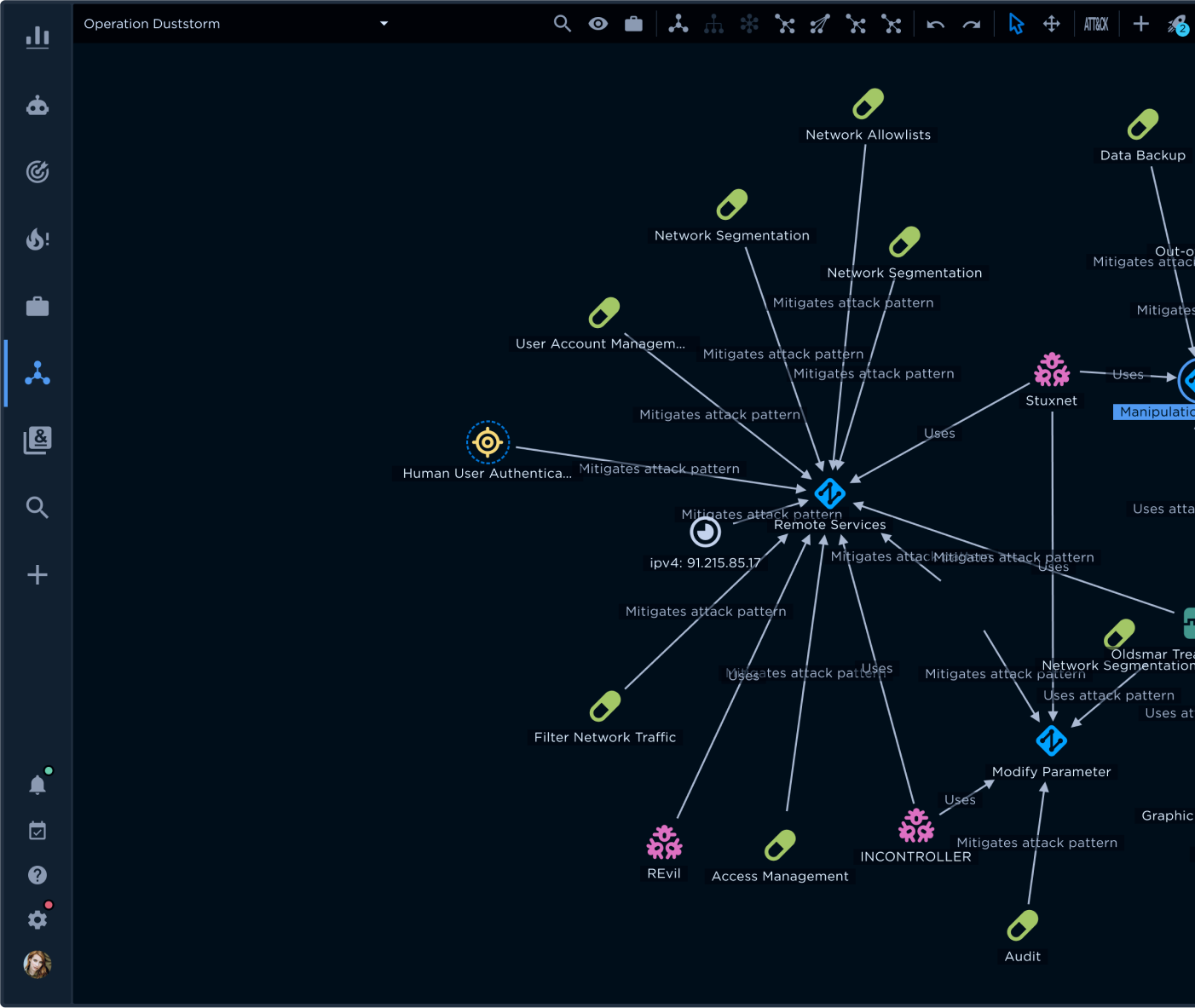
As shown in Figure 1, SolarWinds paints a complex picture. This graph, built from the EclecticIQ Intelligence Center threat database, illustrates the most critical relationships, entities, and observables after processing thousands of data points from multiple open sources and commercial feeds.
Manually processing this volume of data to discern the relevant relationships in time to act is impossible. Yet, that is how many organizations approach this. Though it may sound preposterous, as we noted in "Three Steps to Aligning CTI, SOC, and IR for Action," most organizations still rely on spreadsheets and emails as the primary means to aggregate, analyze, and present CTI information! This reality points to the first step of the early warning protocol.
Step One: prioritize and centralize your CTI to cut through the noise
You need a scalable threat intelligence management platform that automatically normalizes, deduplicates, and prioritizes vast amounts of structured and unstructured threat data. Such a platform will help you pull the signal from the noise.
There is a lot of noise with threat intelligence. The volume of data is enormous, with new feed providers coming online regularly. To give some perspective, EclecticIQ clients typically process millions of entities and observables each month.
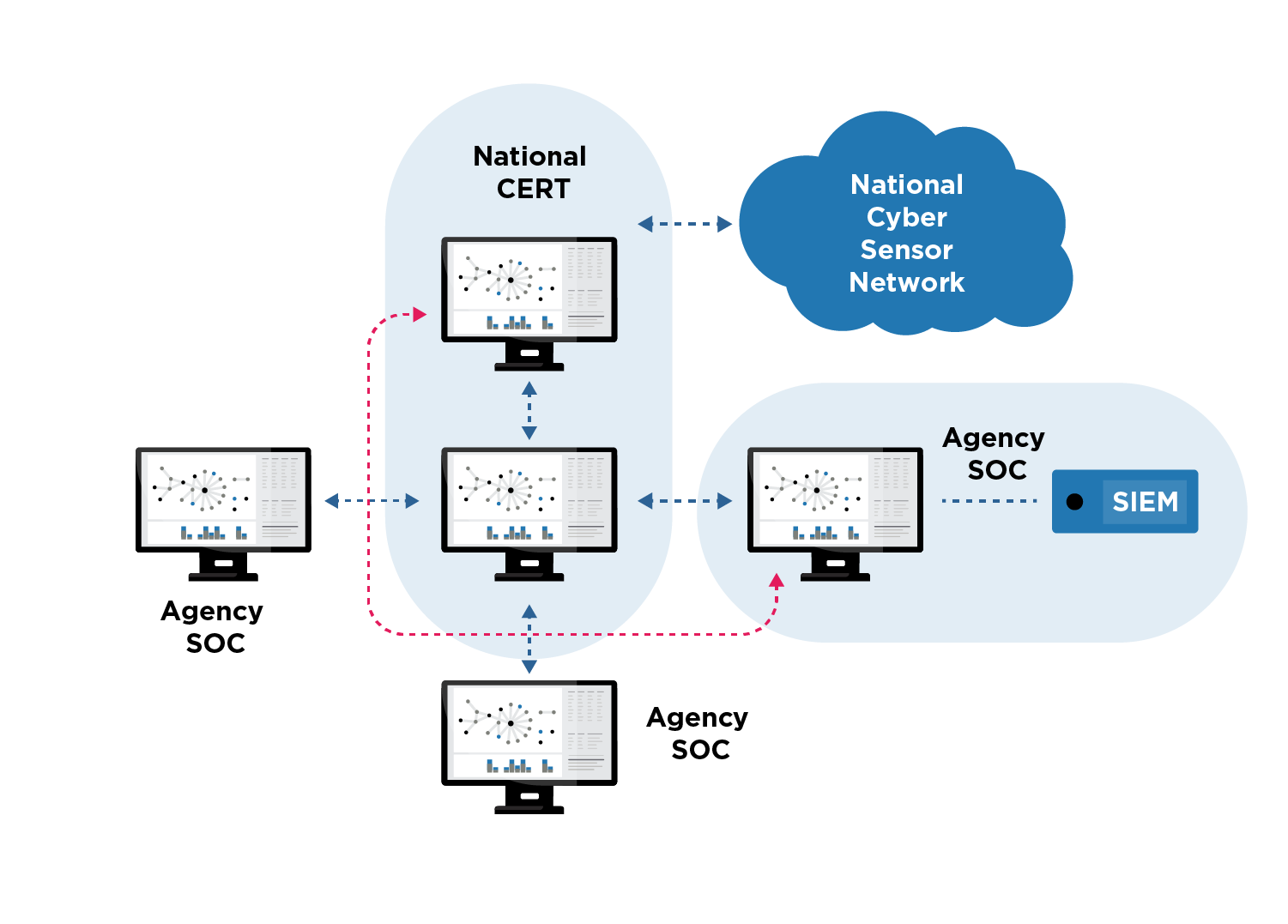
In addition to offering robust data processing capability, the platform you choose should match your organization's workflow and those of your partners, suppliers, and constituents. For example, as shown in Figure 2, a national Computer Emergency Response Team (CERT) deployed EclecticIQ Intelligence Center in a hub-and-spoke architecture with instances installed at the SOC of each agency the CERT supports. These instances communicate with a central hub instance. This implementation optimizes data sharing and collaboration with the agencies.
A hub-and-spoke design works well for peer-to-peer organizational relationships. However, many supply chain situations call for a hierarchical structure for collaboration and sharing of threat intelligence. This structure addresses the challenges of limited cybersecurity skills among your supply chain members.
To accommodate these different workflow needs, look for a platform with the flexibility to support any architecture.
Now, let's dive into using a solution like EclecticIQ Intelligence Center to conduct threat analysis for early warning. EclecticIQ Intelligence Center gives you the ability to explore structured and unstructured Intelligence and produce context-rich CTI. It allows you to quickly connect entity types and relationships to convey additional context. You can then pivot on that information to conduct a deeper investigation. To illustrate the value of such a platform for establishing early warning, let's turn the clock back to 2019.
A seemingly isolated event?
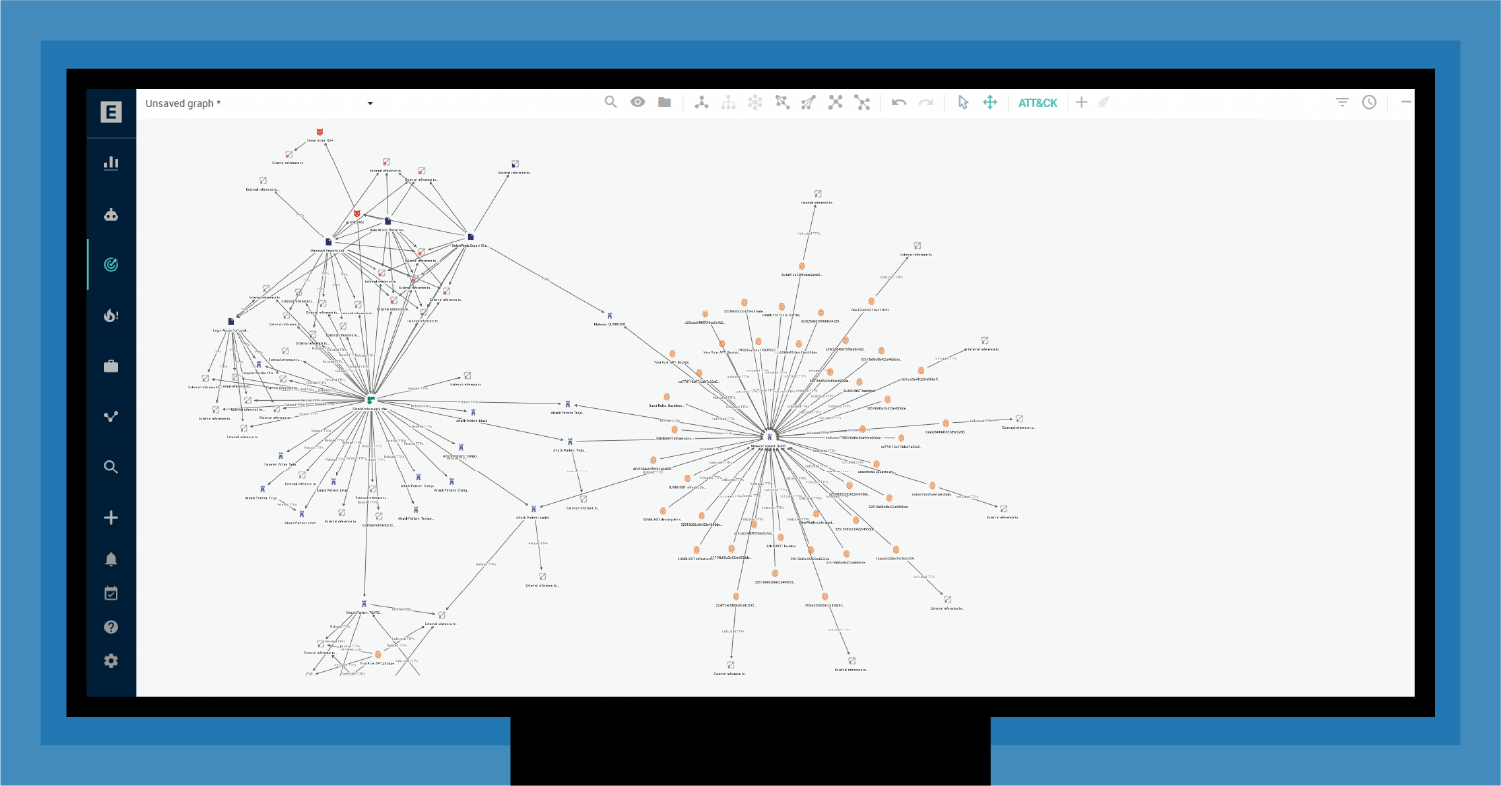
In early 2019, EclecticIQ Intelligence Center customers got a hint that something bad was happening when two pieces of malware appeared on their platform instance. Today, we identify the malware as SunSpot and Sunburst. One (SunSpot) monitors the build process of the Orion platform and injects the second malware (SunBurst) into that build process. Sunburst is a super-stealthy, obfuscated backdoor that becomes the gateway for malicious access to IT systems.
What should EclecticIQ Intelligence Center customers have done? Best practice would have been isolating the associated indicators of compromise (IOCs) for their SOC to block command and control (C2) communications. And for many, this would have been the end of the story: they identified and responded to a sophisticated APT. However, it was just the beginning, as we now know.
Step Two: leverage the power of community
Very few organizations have the internal resources and external inputs to see beyond what's right in front of them (i.e., two pieces of advanced malware). Even large government agencies lack the resources and visibility to manage an attack like SolarWinds without cooperative input from other organizations.
Only when you see the whole picture can you understand the scope of the attack. This is where early warning is so helpful. An early warning protocol provides essential information to fill in the gaps in your picture. The sooner you can fill in those gaps, the greater your ability to respond.
One EclecticIQ customer has developed an early warning protocol for his global bank by establishing an over-the-horizon view. He collaborates with others that can see aspects of the threat landscape beyond his perspective: government organizations (UK National CERT and NCSC), peer organizations (financial services ISAC), and members of his supply chain.
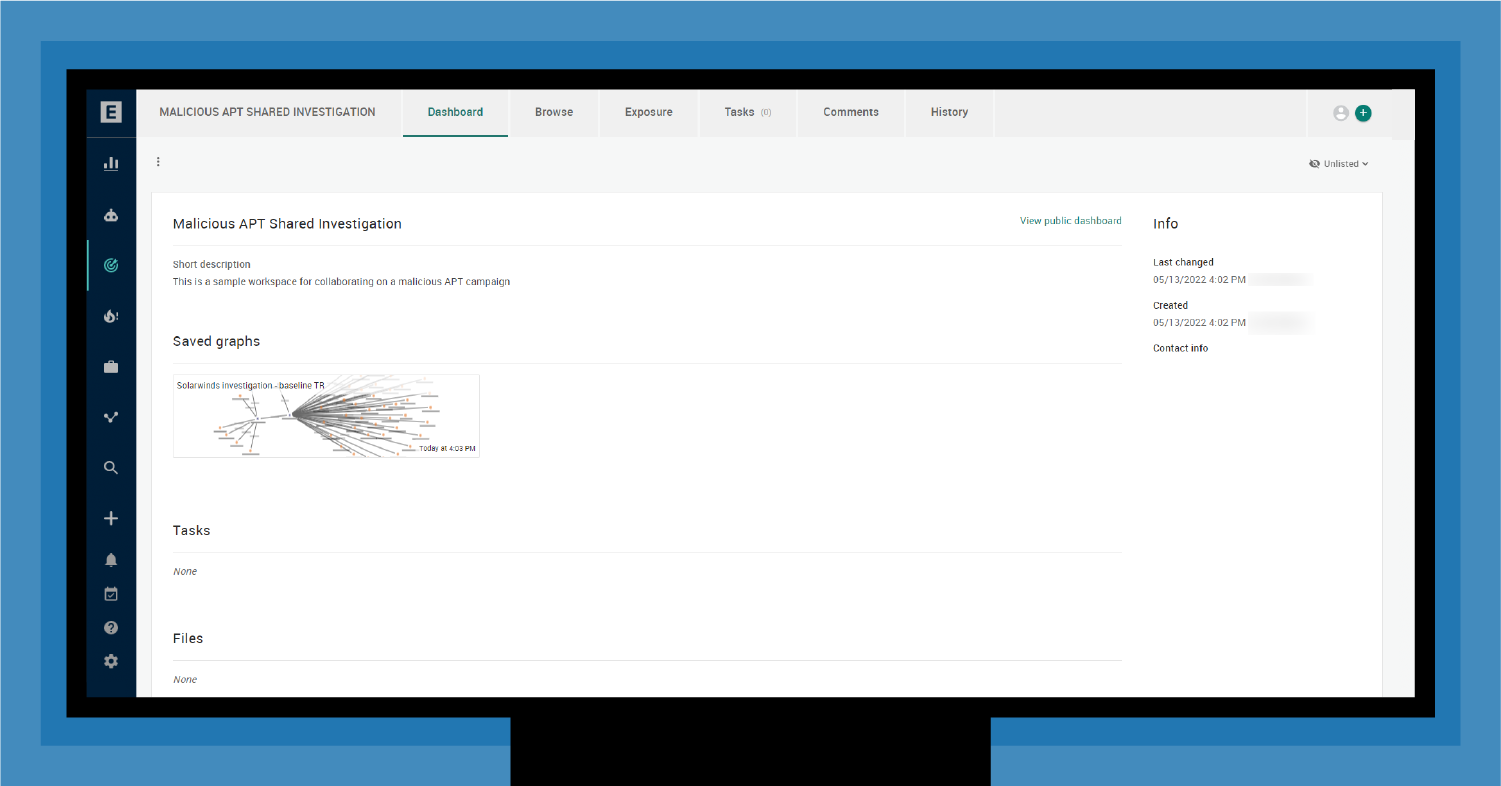
Conducting collaboration for early warning requires a shared workspace. As shown in Figure 4, EclecticIQ Intelligence Center provides a secure, shared workspace featuring federated security and trust mechanisms with role-based access controls (RBAC) to manage access to confidential data among participants. Each organization controls access to its data.
This shared workspace becomes the central whiteboard for your investigation.
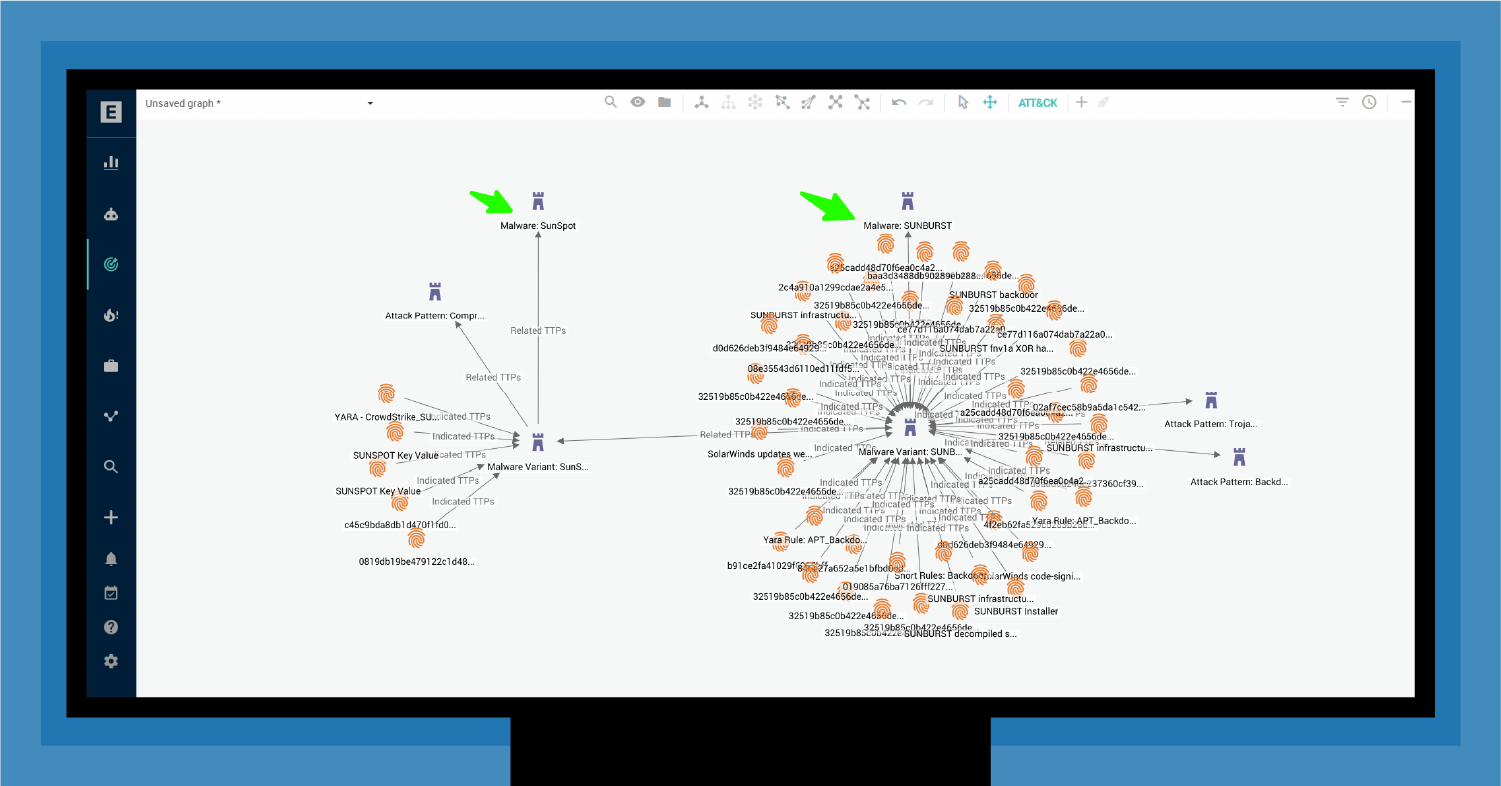
Returning to 2019 and the SunSpot/SunBurst threat, a supply chain partner might have had access to relevant threat intelligence. For example, a partner that ran a dedicated Microsoft shop would have closely monitored for alerts on threats to the Windows OS.
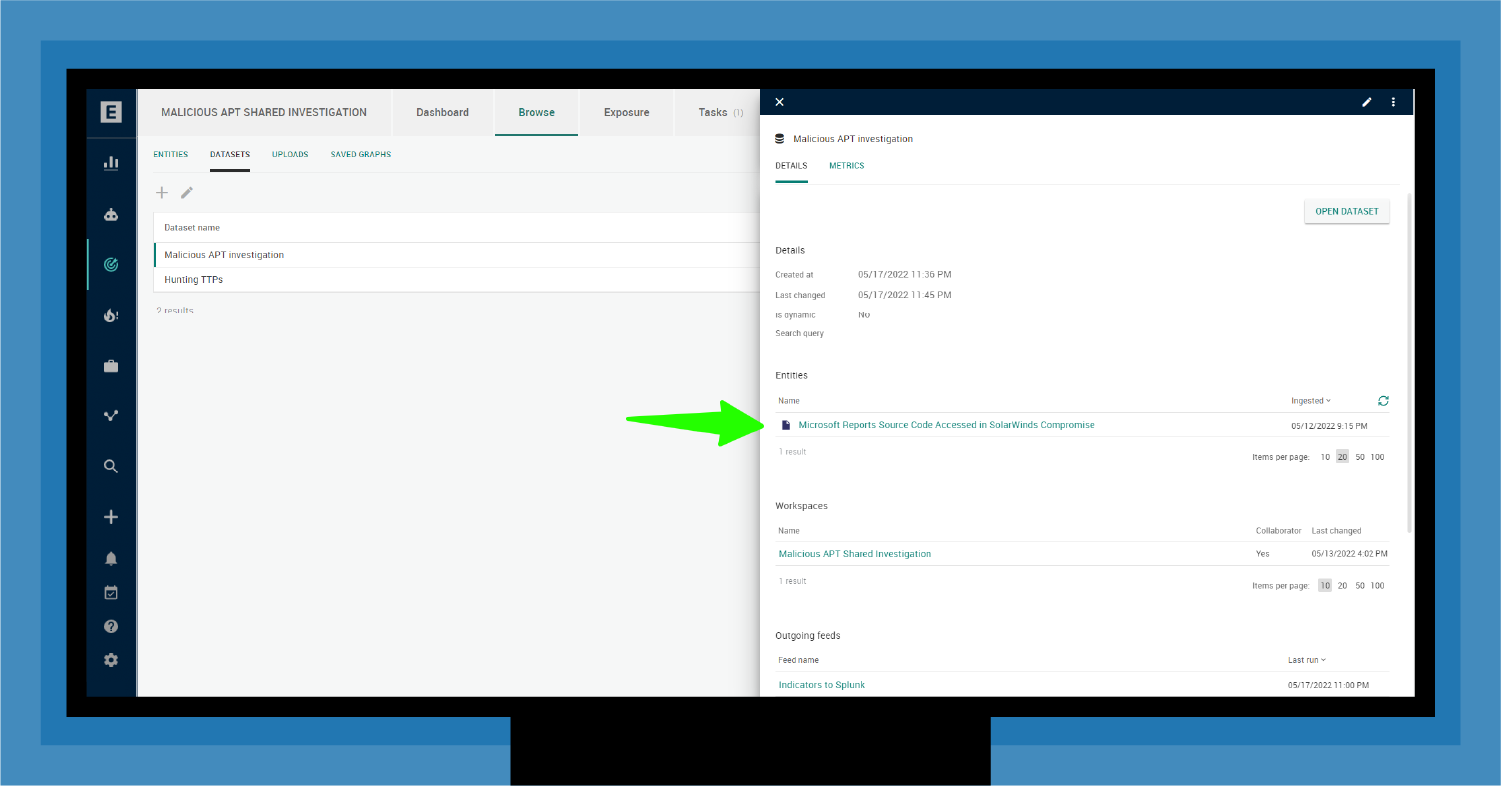
As shown in Figure 5, this partner could have added an entity to the dataset in the shared workspace highlighting how Microsoft discovered similar malware on its servers.
In this case, the reported Microsoft compromise would tell everyone that the threat actors behind this malware must be pretty sophisticated (they broke through Microsoft defenses) and target huge organizations.
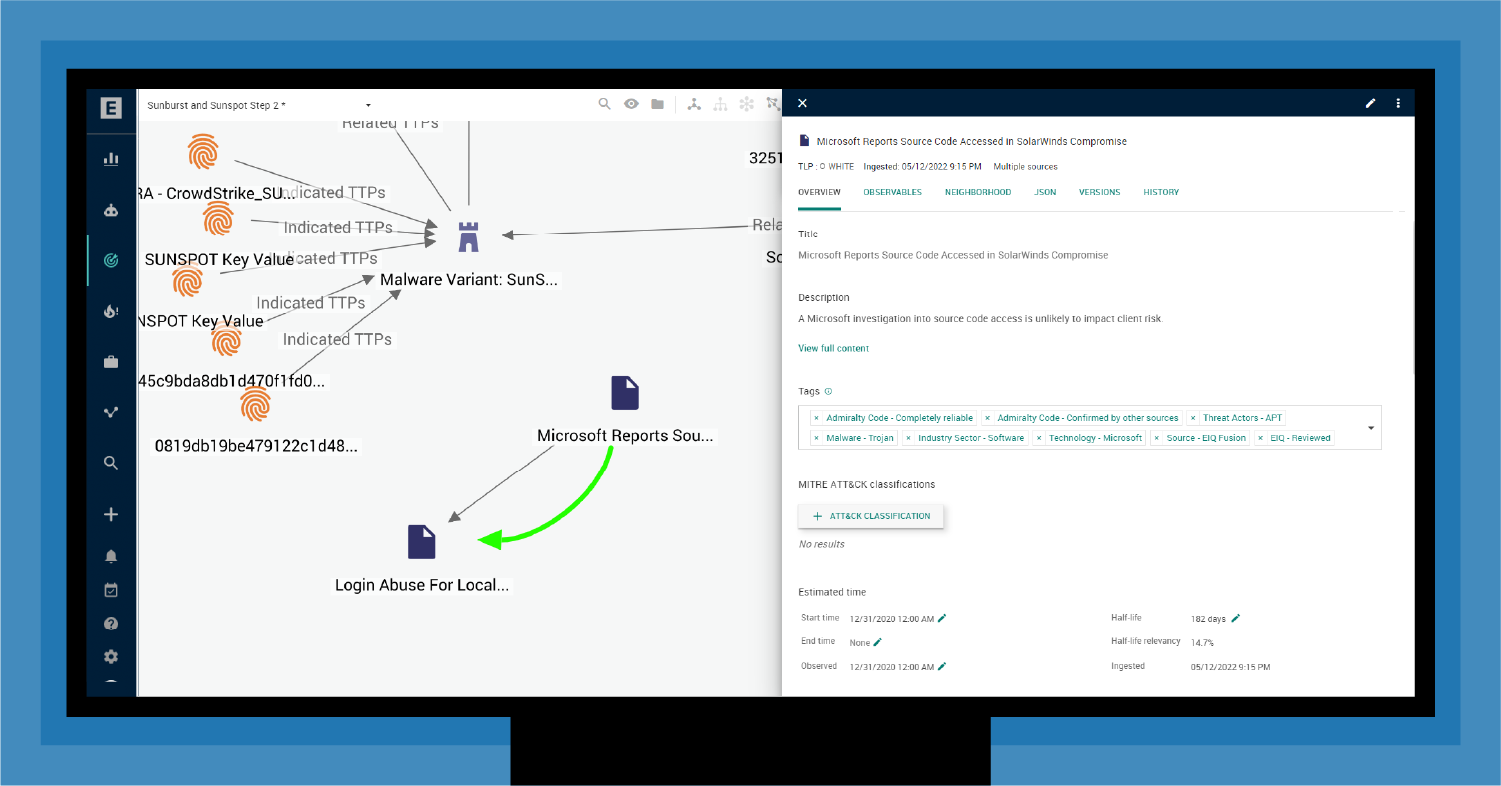
As shown in Figure 6, the reported Microsoft compromise was similar to the malware seen by EclecticIQ customers. EclecticIQ Intelligence Center automatically linked this report with a National Security Agency (NSA) report about login abuse for local cloud admin accounts aligning to the same TTPs. However, there wasn't sufficient information to directly connect the malware EclecticIQ customers were seeing and what Microsoft was allegedly seeing.
Though this might look like a dead end, it wasn't. Not long after receiving the Microsoft report, another partner in the supply chain received Intelligence that helped to make missing connections.
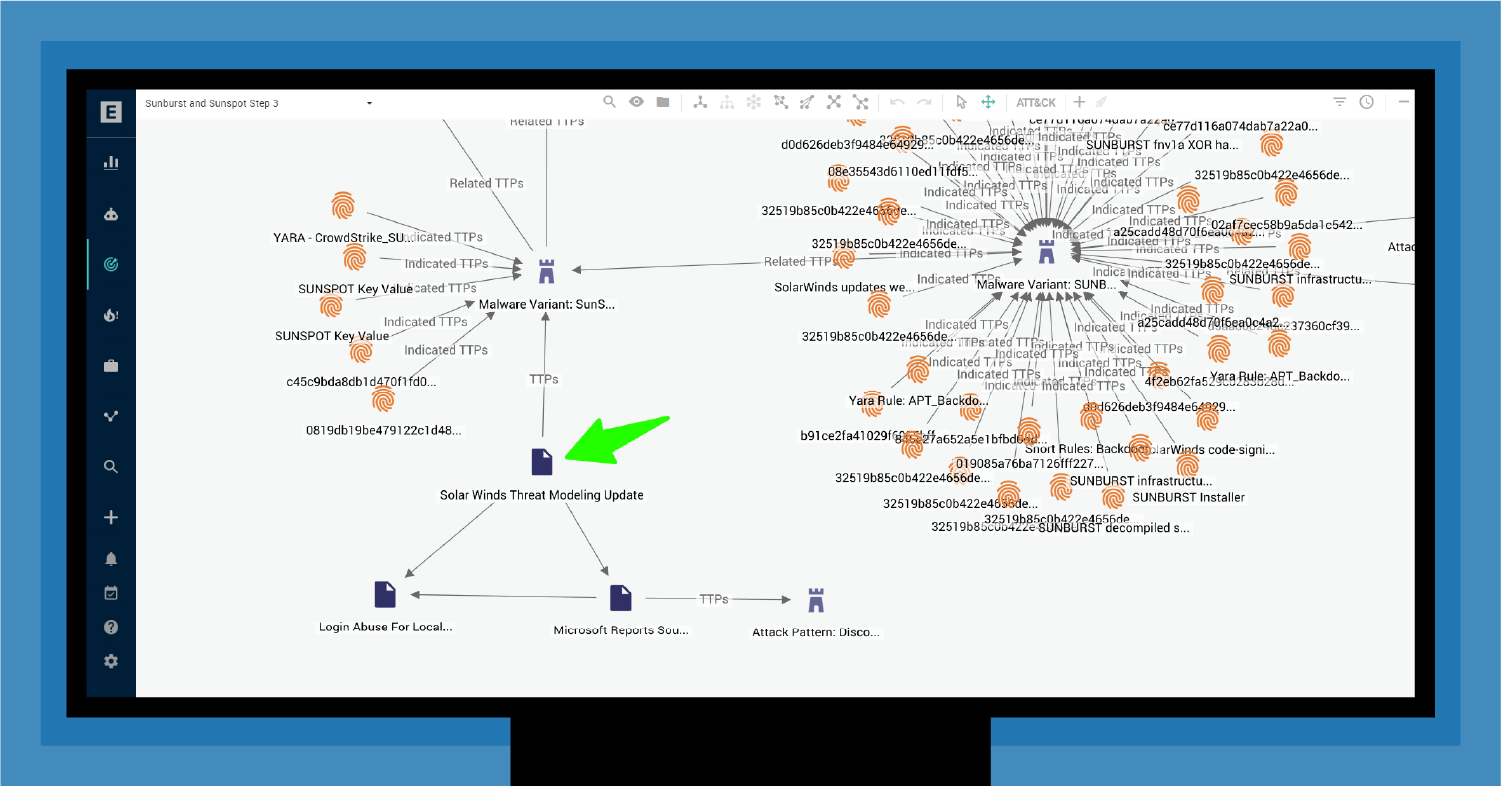
Figure 7 shows a direct alignment between what Microsoft detected and what EclecticIQ Intelligence Center customers could see in their environment. This report would have filled in many gaps and painted a picture of a highly advanced, malicious, and stealthy threat campaign, which turned out to be SolarWinds.
Further analysis of this newly connected intelligence through collaboration with the supply chain and automatic prioritization of intelligence data by EclecticIQ Intelligence Center would have clarified the picture even more.
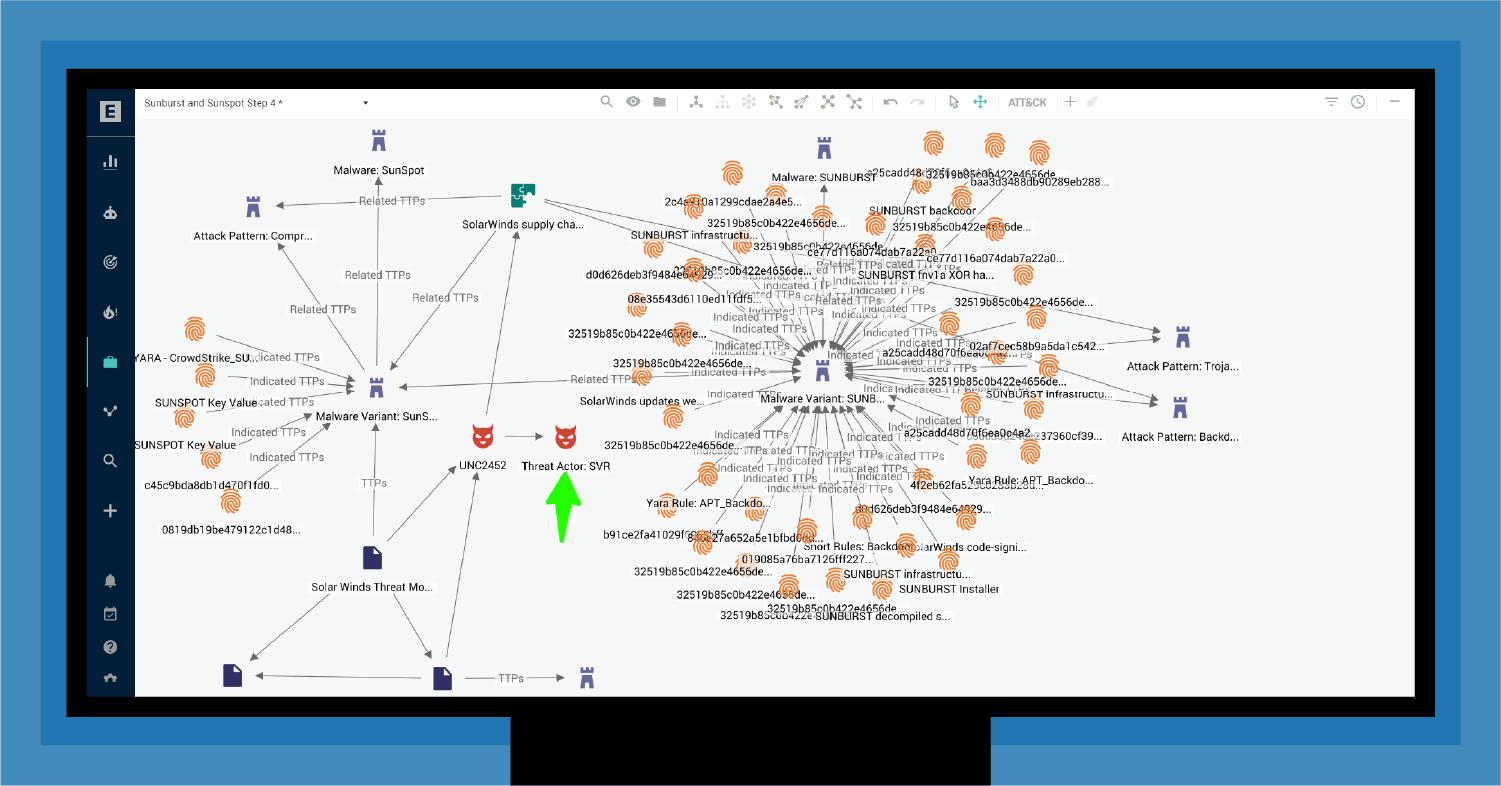
SolarWinds connected through intermediary threat actors to SVR, Russia's foreign intelligence service (Fig. 8), indicating the need to defend against a considerable threat.
Not quite early warning
At this point, EclecticIQ Intelligence Center customers would have achieved most of their early warning goals. Their platform helped prioritize data, filtered the signal from the noise, and provided a collaborative workspace to securely share information. The result would have been reliable CTI about the SolarWinds threat at an early stage.
Step Three: integrate all stakeholders for a coordinated response
Bringing the lessons of 2019 to the present day, once you see an active threat campaign against your enterprise and supply chain, it's time to make this advance knowledge actionable. To do this, you must engage your SOC and threat hunting teams to go after the TTPs associated with the threat.
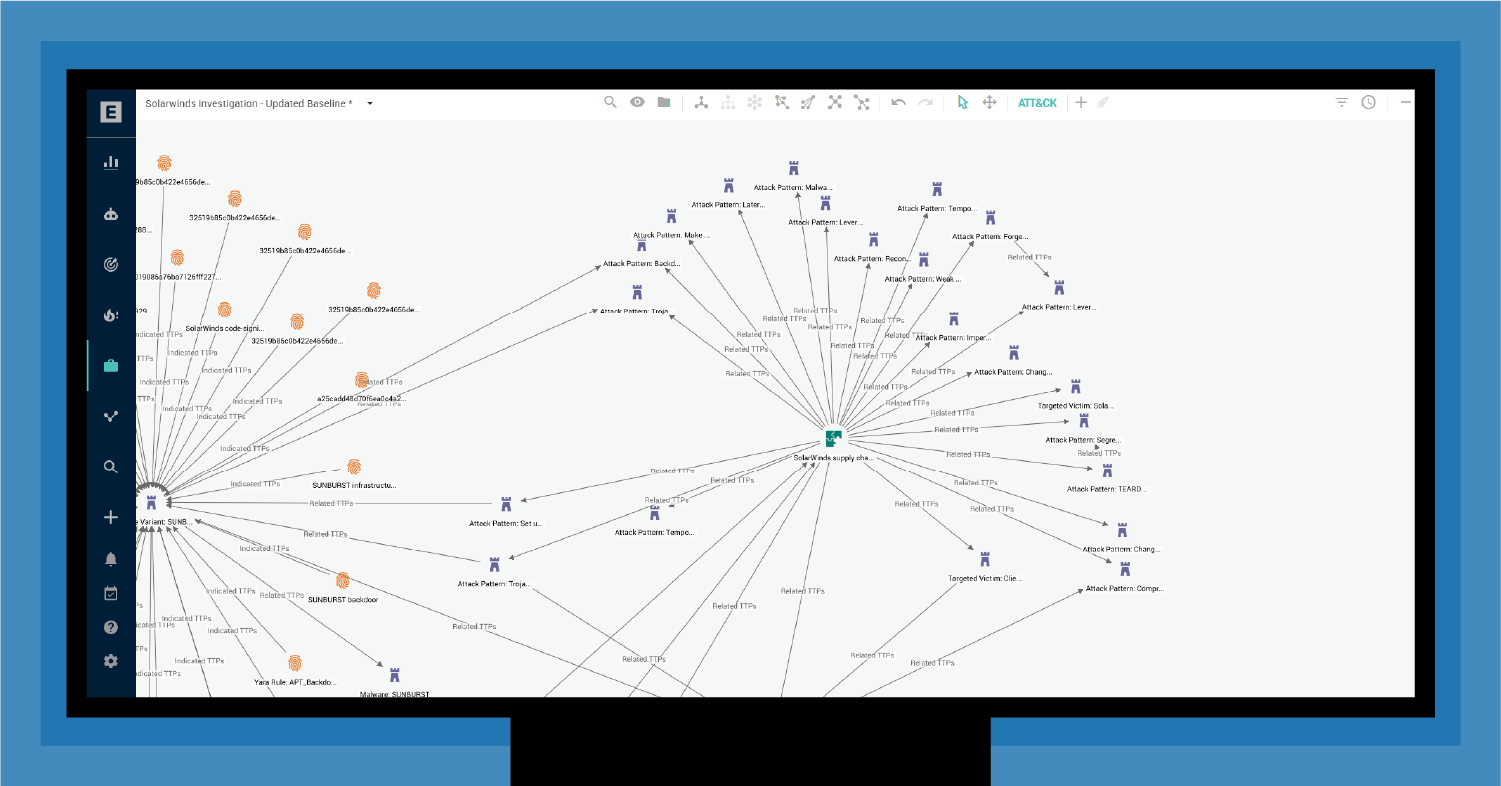
For example, as shown in Figure 9, the SolarWinds campaign included at least 20 TTPs, any of which could have been active in a target organization's network or that of supply chain partners.
Focusing on TTPs is essential for dealing with sophisticated threats like SolarWinds. With EclecticIQ Intelligence Center, you can group these TTPs and assign a task to your workspace that directs your threat hunting team to download the entities and hunt for further active threats. Similarly, you can grab all IOCs with high reliability and pass them to your partners' SOCs to download to their firewalls for immediate blocking. This is the essence of actionable threat intelligence.
It's a two-way street
At this point, you are close to implementing an early warning protocol. You still must quickly identify active attacks on your organization or that of your supply chain partners or constituents. To find active threats you need a two-way integration with your SOC that automatically feeds sightings (IOCs) from the SIEM back into the platform.
Aligning a sighting with an active campaign positions you and your partners to receive reliable information about active exploits. Plus, because you know the associated TTPs, you can prioritize your threat hunting to identify additional exploits as early in the Kill Chain as possible.
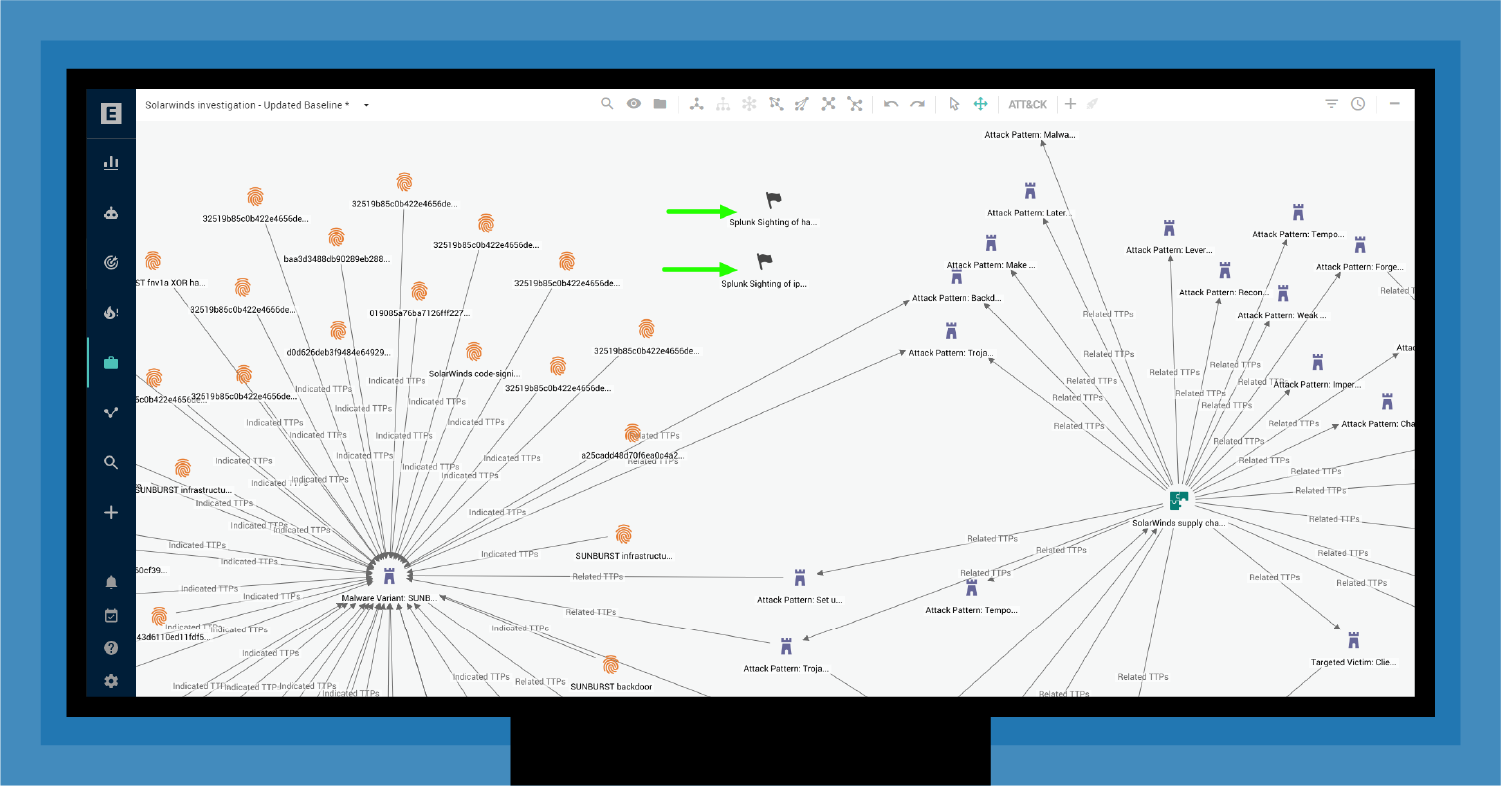
Identifying active campaigns and detecting exploits early in the Kill Chain show early warning in action. As shown in Figure 10, pulling sightings from Splunk directly into your shared workspace helps your CTI and SOC analysts quickly make critical connections between the sightings in your network and your understanding of the broader TTPs associated with a threat campaign like SolarWinds.
Illustrating how this feedback loop works, one of EclecticIQ's clients (the national CERT mentioned above) uses sightings to focus on active campaigns and threat actors. EclecticIQ Intelligence Center passes CTI to the nation's cyber sensor network based on level of confidence, priority, and timeliness. If the CERT team detects observables on the network, it sends sightings to the relevant constituent so that its SOC can hunt down active exploits and block related attacks. From its vantage point, the national CERT can immediately detect threat actors and exploits active in multiple agency networks, meaning a broader, coordinated attack on the national critical infrastructure is likely underway. For more information, see our case study: "EclecticIQ Empowers a National CERT's Collaborative Threat Intelligence Sharing Community."
Establishing your over-the-horizon view
We've covered a lot of ground using SolarWinds as our guide. In 2019, an apparently limited attack using sophisticated malware turned out to be one of the gravest attacks against global supply chains to date. As we illustrated, deploying a scalable and extensible CTI platform, creating a central shared workspace, and creating reliable and actionable CTI allows you to establish an over-the-horizon view and develop an early warning protocol for your collaboration partners.