For SOC Teams
Enable your SOC team to better operationalize threat intelligence for more effective and efficient incident response with our range of analyst-centric management products and services.
CHallenge
SOC teams are hard-pressed to protect the organization due to significant challenges of alert fatigue, staff shortages, and ineffective tooling.
These short-staffed teams face a continual deluge of alerts driving alert fatigue and leading teams to either tune their security information and event manager (SIEM) to squelch alerts or waste all their limited time chasing false positives.
The former approach lets adversaries fly under the radar, and the latter emboldens adversaries as analysts are too distracted to detect and respond in time to stop the threat. Plus, even when the SIEM sees an adversary, SOC tools typically lack the visibility of the threat landscape to analyze, let alone eliminate adversarial capabilities successfully.
Solution
The cyber skills shortage is not going away, so SOC teams must optimize their limited resources by pivoting from a reactive alert-led to a proactive intelligence-led operation. This shift hinges on the SOC operationalizing threat intelligence to better hunt and detect the most significant threats and avoid or eliminate them.
Operationalizing threat intelligence boosts SIEM effectiveness and saves hours of SOC analyst time by closely aligning with a threat intelligence management solution to better qualify alerts and reduce false positives. Central to this intelligence-led approach is SOC analysts focusing on tactics, techniques, and procedures (TTPs). This pivot to TTPs empowers analysts to be more efficient and effective, moving from the most obvious threats to hunting and catching the most elusive threats, including advanced persistent threats (APTs).
Approach
With EclecticIQ, SOCs operationalize threat intelligence via a range of analyst-centric threat intelligence management products and services that tightly integrate with the organization’s SIEM, security controls, and other SOC systems. Critical characteristics of EclecticIQ’s approach to intelligence-led SOC operation are:
-
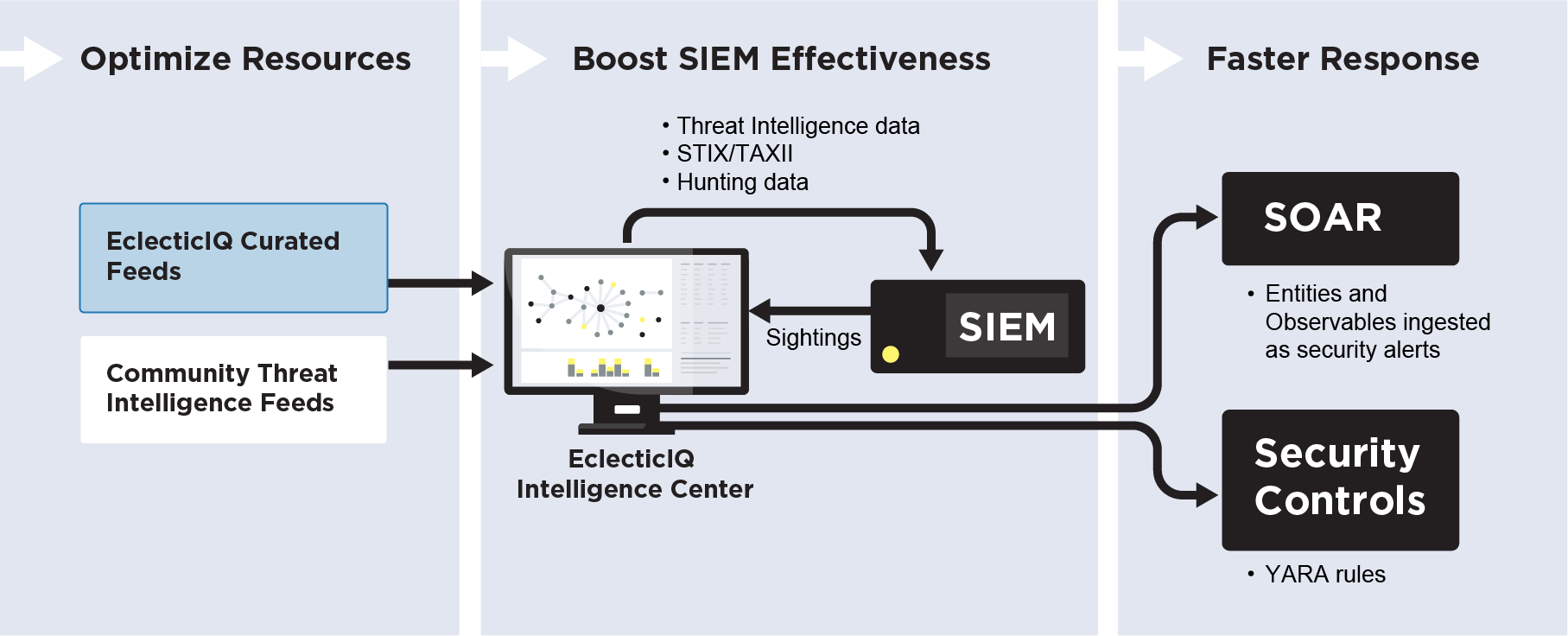
Enriching SIEM Alerts
With threat intelligence for qualification and reduction of false positives. EclecticIQ maintains the full context of all data.
Read moreWith threat intelligence for qualification and reduction of false positives. EclecticIQ maintains the full context of all data.
-
Integrating SIEM Communications
To automatically feed sightings back into EclecticIQ Intelligence Center and pass data to security controls to effectively block valid ... Read more
To automatically feed sightings back into EclecticIQ Intelligence Center and pass data to security controls to effectively block valid threats.
-
Visualization, Search Tools, and Advanced Threat Hunting Capabilities
To identify elusive attack patterns, active threats, and view incident context for swift detection, analysis, and response.
Read moreTo identify elusive attack patterns, active threats, and view incident context for swift detection, analysis, and response.
-
Providing Tools for Collaboration
Between SOC teams and their network of stakeholders for faster, more coordinated incident response (IR).
Read moreBetween SOC teams and their network of stakeholders for faster, more coordinated incident response (IR).
-
Anonymization of Threat Data
During dissemination and collaboration to protect the confidentiality of data and meet compliance (e.g., GDPR) requirements.
Read moreDuring dissemination and collaboration to protect the confidentiality of data and meet compliance (e.g., GDPR) requirements.
Benefits
With EclecticIQ, SOC teams better leverage their scarce resources and overcome alert overload by shifting from reactive alert-led to proactive intelligence-led SOC operations. Key benefits of this approach include:
- Less time spent chasing false positives and more time addressing active threats, including the most elusive threats.
- Better identifying, tracking, isolating, and mitigating these active threats via tight integration with the SOC’s SIEM and other security controls.
- More effective and efficient incident response through added context provided by a two-way integration between EclecticIQ Intelligence Center and the SIEM.
- Faster response with less effort through a collaborative workspace that uses advanced search and graph capabilities to help analysts track threat actors and align TTPs.
- More proactive SOC operations to get ahead of the threat through advanced threat hunting capabilities.
Related Packages, Products & Services
EclecticIQ TIP for SOC
Run an intelligence-led SOC with the threat intelligence platform that goes beyond the IOC.
EclecticIQ Intelligence Center
Automate threat intelligence management and analyst workflows with the analyst-centric Threat Intelligence Platform.
EclecticIQ Curated Feeds
Track primary threats with curated threat data feeds optimized for EclecticIQ intelligence center.
EclecticIQ Hunting Packs
Advanced cyber threat detection and response made easy.
Threat Intelligence Consultants
Supercharge your threat intelligence operations with expert guidance.
Platform Overview
Discover our unique approach to Intelligence, Automation and Collaboration.
Intelligence at the core™
Stay ahead of rapidly evolving threats and outmaneuver your adversaries.
-
Threat Intelligence Platform For SOC Package
The EclecticIQ TIP for SOC package enables enterprises and government agencies to pivot from a reactive, alert-led operation to a proactive, intelligence-led operation. With this pivot, SOC teams overcome the overwhelming flood of alerts and IOCs to focus on adversary tactics, techniques, and procedures (TTPs).
Download Product Description
EclecticIQ is trusted by the best in cybersecurity




